On Ruinous Misperception of Biometrics

Here are some of my recent writings about the misperception on security-ruining biometrics.
‘Not as secure as claimed’ is one thing. ‘Harmful to security’ is another.
Probabilistic Is Human Body, Not Pattern-Matching Algorithm
US Army appears tobe scarily misguided
AI-Enhanced Biometrics – How Dreadful?
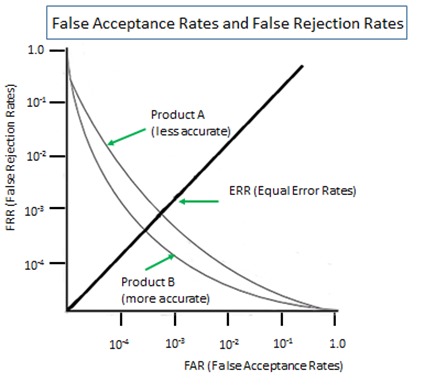
Quantitative Examination of Multiple Authenticator Deployment
It appears that there are so many security professionals who pay no attention to the exactly opposite effects of 'multi-layer' and 'multi-entrance deployments. ‘Multi-Layer’ is also represented by ‘In-Series’, ‘In-Addition-To’, ‘All/BothAnd’ and ‘Conjunction’ in logic, while ‘Multi-Entrance’ by ‘In-Parallel’, ‘In-Stead-Of’, ‘EitherOr’ and ‘Disjunction’. Let me offer a quantitative examination of multiple authenticators deployed in two different ways.
Vulnerability (attack surface) of an authenticator is generally presented as a figure between 0 and 1. The larger the figure is, the larger the attack surface is, i.e., the more vulnerable. Assume, for instance, as just a thought experiment, that the vulnerability of the PKI-enabled token (x) be 1/10,000 and that of the password (y) be 10 times more vulnerable, say. 1/1,000. When the two are deployed in ‘multi-layer’ method, the total vulnerability (attack surface) is the product of the two, say, (x) and (y) multiplied. The figure of 1/10,000,000 means it is 1,000 times more secure than (x) alone.
On the other hand, when the two are authenticators deployed in ‘multi-entrance’ method, the total vulnerability (attack surface) is obtained by (x) + (y) – (xy), approximately 0.0011. It is about 11 times less secure than (x) alone.
So long as the figures are below 1, whatever figures are given to (x) and (y), deployment of 2 authenticators in ‘multi-layer’ method brings higher security while ‘multi-entrance’ deployment brings lower security. As such ‘multi-layer’ and ‘multi-entrance’ must be distinctly separated when talking about security effects of multiple authenticators.
Remark: Some people may wonder why (xy) is deducted from the sum of (x)+(y).
When (x) and (y) is very small, the (xy) is very close to 0, which we can practically ignore. But we should not ignore it when the figures are considerably large.
Suppose a case that both the two authenticators are deployed in an extremely careless manner, for instance, that the attack surfaces of (x) and (y) reach 70% (0.7) and 60% (0.6) respectively. If simply added the figure would be 130% (1.3). It conflicts with the starting proposition the figures being between 0 and 1.
Imagine a white surface area. Painting 70% of it in black leaves 30% white surface. Painting 60% of the remaining 30% in black will result in 88% black and 12% white surfaces. Painting 60% first in black and then painting 70% of the remaining 40% brings the same result of 88% black and 12% white. So does “(x)+(y)-(xy)”. The overall vulnerability (attack surface) is 0.88 (88%) in this case.
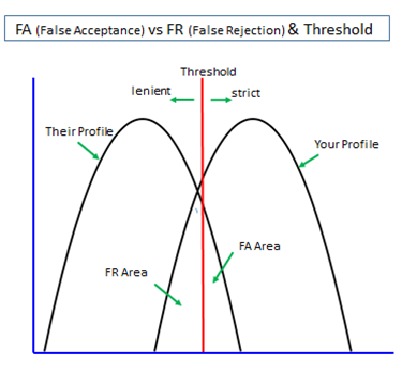
The same calculation applies to biometrics used in cyber space where it has to rely on a fallback password/PIN deployed in ‘multi-entrance’ method against false rejection. You might assume that biometrics deployed with a password/PIN in ‘multi-layer’ method should bring us a very high security. But, very sadly, this scenario never comes true. When rejected by biometrics, what can we do? We will only see that we are unable to login even if we can feed our password/PIN.
Hitoshi Kokumaiの記事
ブログを見る
The quantum computer held in a bad guy’s hand is indeed a big threat. So is the artificial intellige ...

Bad guys, who have a quantum computer at hand, would still have to break the part of user authentica ...
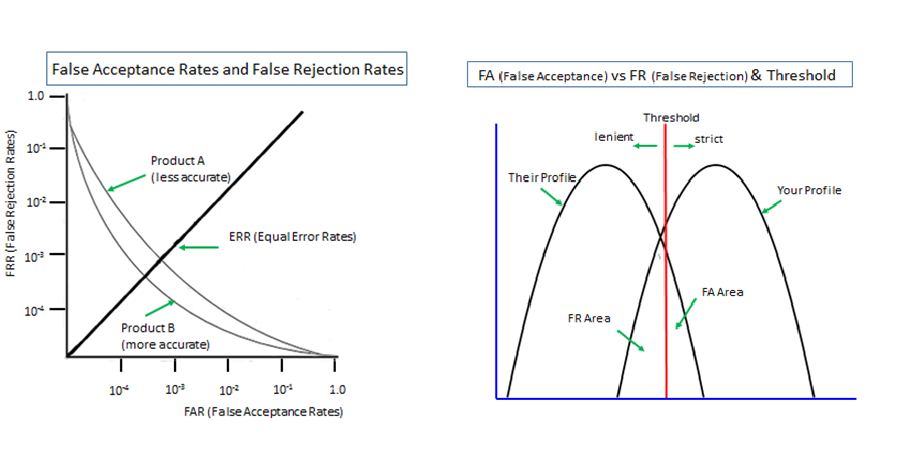
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...
この職種に興味がある方はこちら
-

現場監督・工事管理
1日前
公開範囲1.等を含む求人情報を公開する Aomori, 日本 フルタイム仕事内容 · *現場管理 · *営業 · *資機材管理 · *書類作成(パソコン使用) · *移動には社用車を使用します 雇用形態 正社員 派遣・請負等 就業形態 派遣・請負ではない 雇用期間 雇用期間の定めなし 就業場所 〒 青森県青森市奥野4丁目17-18 最寄り駅 青森駅 最寄り駅から就業場所までの交通手段 車 所要時間 10分 受動喫煙対策 なし(喫煙可) マイカー通勤 マイカー通勤 可 駐車場の有無 あり 転勤の可能性 転勤の可能性 ...
-

調理・販売スタッフ
1日前
公開範囲1.等を含む求人情報を公開する Goshogawara, 日本 パート仕事内容 · ・ハンバーガー類の調理 · ・ハンバーガー類の販売、レジ · ・搬入作業や調理器具洗浄等の簡単な業務 · *未経験者の方の応募を歓迎します · 担当者が丁寧に指導しますので、安心してご応募下さい。 雇用形態 パート労働者 正社員登用の有無 あり 正社員登用の実績(過去3年間) 1名 派遣・請負等 就業形態 派遣・請負ではない 雇用期間 雇用期間の定めあり(4ヶ月未満) 〜2023年3月31日 契約更新の可能性 あり(原則更新) 就業場所 就業場所 事業所所在地と同じ 〒 青森 ...
-
EQS Group Kochi, 日本 フルタイムJOIN OUR TEAM · The EQS Product design Team is looking for new colleague Are you crazy about amazing digital design and believe that B2B users also deserve a super easy user experience? Come and join us and change the way we do Product Design together. Experience is important, b ...

コメント