Truly Big Threat

The quantum computer held in a bad guy’s hand is indeed a big threat. So is the artificial intelligence that has gone out of control.
However, a yet bigger threat comes from the humans who are indifferent to the power and value of humans' volition and memory.
Worst would be the attempt to kick out our volition and memory from digital identity and identity assurance. It would kill the chances for humans to rein in the runaway AI and the abused quantum computing.
Furthermore, democracy is fatally eroded where our identity is established without our volition and memory confirmed,
For more, click “Publishing by aiTech Trend” on Quantum Computing and AI

Key References
Biometrics is to Password what Back door is to Front door
Removal of Passwords and Its Security Effect
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’
Additional References
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
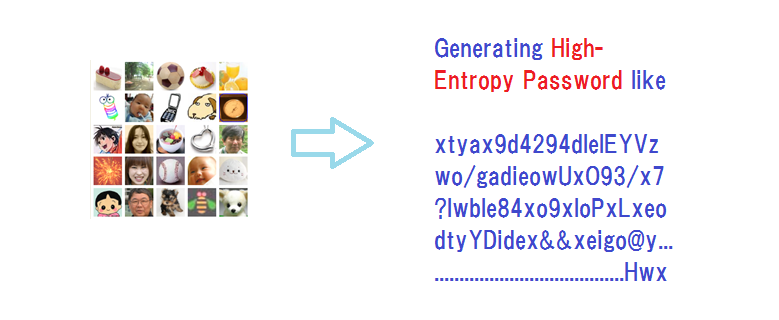
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Account Recovery with Expanded Password System
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues

< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
Hitoshi Kokumaiの記事
ブログを見る
We today take up this report “NSA: We 'don't know when or even if' a quantum computer will ever be a ...
We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password sys ...
“Expanded Password System is no bad, but we do not need it. · We can rely on password managers that ...
この職種に興味がある方はこちら
-
セブン-イレブン 市原菊間店
次の場所にあります: Talent JP C2 - 1日前
株式会社セブン - イレブン・ジャパン Ichihara, 日本レジで一番大事なのは、元気な声と「笑顔」です。バーコードをピッとあてるだけで、操作はとっても簡単なので未経験でも安心 · セブン-イレブンのコンビニスタッフ求人です。接客、販売をはじめ商品の補充や店内清掃など。ほかにも、公共料金の支払いや宅配便の荷受けに各種店頭受け取りサービスなど、幅広い仕事がありますが、丁寧にお教えし、徐々に覚えていただきますので安心して、ご応募ください。 · ...
-

人事(採用・教育)
次の場所にあります: Whatjobs JP C2 - 5日前
航空集配ホールディングス株式会社 習志野市, 日本航空集配ホールディングス株式会社 · 【千葉/習志野】人事総務(新卒採用メイン)※未経験歓迎/残業月10h程/土日祝休み · 【仕事内容】 · 【千葉/習志野】人事総務(新卒採用メイン)※未経験歓迎/残業月10h程/土日祝休み · 【具体的な仕事内容】 · - 担当業務: · ホールディングスの人事担当として、新卒採用を中心に、将来にわたり幅広く業務を担っていただきます。 · - 業務内容: · 新卒採用業務からスタートいただき、徐々に下記に記載の総務人事系の業務を幅広く担っていただきます。 · 採用業務、給与計算業務、労務管理、法務業務、福利厚生全般管 ...
-

カスタマーサポート
次の場所にあります: Whatjobs JP C2 - 5日前
株式会社TOKI 豊島区 東池袋, 日本【職種名】 · 完全土日祝休み内定まで2週間不動産のアポイント獲得業務 · **仕事内容**: · 不動産のアポイント獲得業務 · 見込み顧客に対して【反響営業】を電話口で行う業務 · ※不動産の知識がなくてもコミュニケーションスキルを活かしてすぐに活躍できる環境が整っています。 · **勤務地**: · 東京都豊島区東池袋2-60-2池袋パークハイツ2F · **勤務時間**: · 固定時間制 · 09:00 ~ 18:00 · 実働時間:8時間/日 · **給与**: · 時給 1600円 ~ 1700円 · **休日休暇**: · 完全週休2日制 ...

コメント