Negative Security Effect of Biometrics Deployed in Cyberspace

It was in 2001 on the website of a globally reputed electronics manufacturer that I first noticed this awkward phenomenon. They alleged that their face biometrics was going to displace the password. It immediately occurred to me what we could do when the system failed to recognize us. I quickly started to search for an answer on their website and found a brief statement in a Q&A corner "Don't worry if you are not recognized. You can get logged in by feeding the password that you had registered earlier".
The second encounter came a few months later at a security conference where another global brand hung a large poster reading "Farewell to Password by Fingerprints". I asked an attendant "What can we do when rejected by the fingerprints sensor?", to which he replied "Don't worry. You can rescue yourself by feeding the password that had been registered earlier". I raised the next question "Then, how would it be possible for you to allege "Farewell to Password by Fingerprints?” The attendant turned silent and never opened his mouth again. I gave up and left there.
It has been as such since 2001 and still is.
Below are the agenda to be discussed in this article.
- A default/fallback password is the password, isn’t it?
- Convenience is doubled-edged
- Spoofing and Liveness-Detection
- Is the password weaker than biometrics?
- Is biometrics-only authentication achievable?
-What can we gain from bringing in biometrics into multi-factor authentication?
- Intermezzo: Entertaining Security Parodies
- Haven’t the biometrics promoters built a huge sandcastle?
- This false sense of security has been benefiting criminals, hasn’t it?
- This false sense of security has only been benefiting criminals, hasn’t it?
- Hey, Biometrics Guys! Get Provoked!
- Conclusion: The password is insufficient, but not harmful. Biometrics is harmful, and not sufficient. Attempting to make quick money by spreading a false sense of security is ethically dubious and practically suicidal.
A default/fallback password is the password, isn’t it?
Let us infer what biometrics promoters and adopters would assert in order to justify their allegation that biometrics, while depending on the password, can displace the password.
It could be "We are aware that consumers have to rely on a default password as the fallback measure in case of false rejection. But, the consumers can complete the authentication without using the password/pincode when they are not rejected by the biometrics. This observation encourages us to assert that biometrics enables us to achieve a password/pincode-less authentication while providing good convenience to citizens".
What they would not mention is "We are not interested to talk about the reality that the adoption of biometrics has enabled criminals to capitalize on the two entrances placed in a 'multi-entrance' deployment which has brought down security to the level lower than a password/pincode-only authentication. Convenience that we offer actually benefits criminals."
Convenience is doubled-edged
Biometrics promoters have persuaded us into believing that nothing is more convenient than putting your finger on a device or looking into a camera. They do not tell what is behind this convenience - security was brought down to the level lower than a password/pincode only authentication as demonstrated in this 2-minute video - https://youtu.be/wuhB5vxKYlg
Good convenience offered to citizens is often the same as the lowered security offered to criminals. We should note here that criminals' motivation to look for good convenience (=lowered security) is probably far greater than citizen's motivation to enjoy good convenience. We should also bear in mind that this kind of convenience could bring a huge inconvenience; Imagine what sort of inconvenience the victims of security breach would have to suffer.
There is no problem in a convenience-first product being declared as a convenience-first product, but it is ethically wrong if a convenient-first product is disguised as a security-first product.
The structure is so simple and plain. It is a conundrum how come reputed banks and other leading service providers have been so indifferent to such simple and plain facts.
Spoofing and Liveness-Detection
You might have heard about what happened to the latest smartphones with fingerprints scan - http://www.forbes.com/sites/daveywinder/2019/11/02/smartphone-security-alert-as-hackers-claim-any-fingerprint-lock-broken-in-20-minutes/
In view of such big biometrics incidents, ‘Liveness-Detection’ touted as a counter-spoofing measure is reportedly a hot topic now among certain biometrics people. It is not worth it.
Liveness-detection is sometimes discussed as if it were a second layer of security. It is not the case. Body features of living animals are variable. What would the user be expected to do if they got wrongly rejected by the liveness detection? Give up the login altogether? If something else is brought in as a fallback measure, it means that the liveness detection works as a second entrance, not a second layer.
All the counter-spoofing measures including liveness detection is no more than a factor of increasing the False Rejection/Non-Match (FR/FN) rates while possibly contributing to the reduction of False Acceptance/Match (FA/FM) rates. A gain grasped in the right hand could possibly be dropping from the left hand, although it is not possible to quantitatively examine this effect until the specific liveness detection is put to the empirical tests in both indoor and outdoor environments.
Liveness detection has been known to us over 15 year. It was first a built-in thermometer and an infra-red sensing to measure the warm temperature of genuine or spoofed hands, fingers and faces. We were not surprised to hear that those were fooled within hours by curious students who started to warm the spoofed objects. Sensing the presence of heartbeats was also defeated very quickly by smart students. Motion-detection beaten by video as well. We will see what will happen next between the ‘advanced liveness detection’ and the ever inquisitive students.
![FRR (Fal Reyection Rages)
False Acceptance Rates and False Rejection Rates|
FA (Poise Acceptance] v3 FR (False Rejection) & Threshold |
§
10°
RR (Equator Rates)
00 wt
a]
10°](https://contents.bebee.com/users/id/13855668/article/negative-security-effect-of-biometrics-deployed-in-cyberspace/231f936f.png)
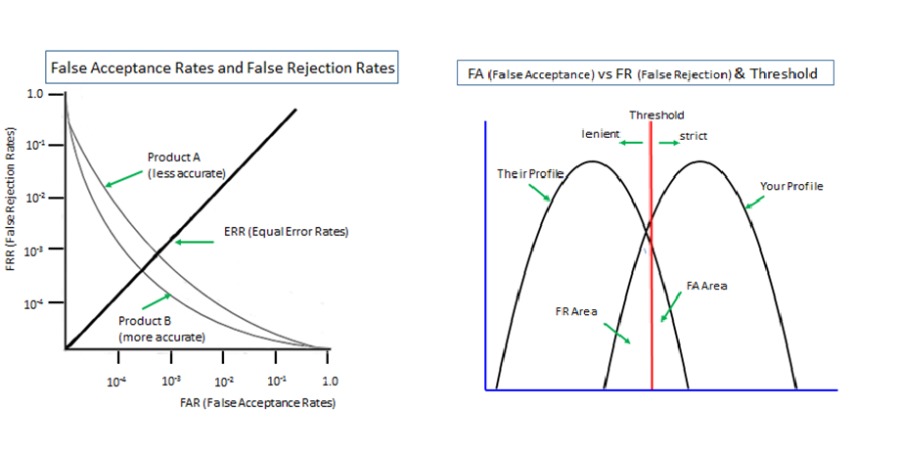
Is the password weaker than biometrics?
It is not feasible to compare a biometrics on its own, which is probabilistic, with a password on its own, which is deterministic. And, in reality, how can we select the test samples to compare from among numerous possible combinations, say, between the two extremes of ‘the securest password vs the least accurate biometrics’ and ‘the poorest password vs the most accurate biometrics’?
If we hear someone speaking that biometrics is more secure than passwords, we should doubt their integrity.
Is biometrics-only authentication achievable?
If taken narrowly and literally, 'biometrics-only authentication' could bring such tragedies as reported in India and examined in this article - "Unnecessary Deaths Presumably Brought By Biometrics Misunderstood" - http://www.valuewalk.com/2018/02/biometrics-aadhaar-danger/

It also brings a 1984-like Dystopia. Democracy is dead where our identity is authenticated without having our will/volition confirmed.
If taken broadly and ambiguously as 'biometrics-only authentication that is backed up by a default/fallback password/pincode', it only brings security down to the level lower than a password/pincode-only authentication as analyzed in the above video and in this article - "Early models of smartphones were safer than newer models - How come?"
What can we gain from bringing in biometrics into multi-factor authentication?
A password and a physical token can be used on its own and also used as a second layer in 'multi-layer' deployment, whereas biometrics cannot be used on its own but must always be used with another authenticator in 'multi-entrance' deployment.
This means that biometrics cannot be a factor of the true multi-factor authentication that is supposed to be deployed in a security-enhancing 'multi-layer' method. Biometrics-involved multi-factor authentications would inevitably bring down the security that could otherwise be maintained.

We often hear professionals say that we should not make a ruling on biometrics by looking at its current performance but we should take it into account that biometrics technologies is improving.
What would you say if you hear pharmaceutical companies stating "We recommend this drug for your healthier life. At present this drug is harmful to your health but we expect that it will evolve to become really effective sometime in the future. So please take this drug now"?
++++++++++++++++++++++++++++++++++++++++++++++++++++++
Intermezzo: Entertaining Security Parodies
Current foot brakes are far from sufficient in the slip distance. This means that the foot brake system is dangerous. We have now removed the dangerous foot brake system from the cars we sell. We instead offer the safer cars that are equipped with better steering handles, better acceleration pedals and better hand brakes.

Physical keys are often stolen, copied and abused. This means that the lock/key system is dangerous. We have now removed the dangerous lock/key system from the houses that we sell. We instead protect our houses by making the door panels thicker and heavier
Passwords are often stolen, leaked and abused. This means that the password system is dangerous. We have now removed the dangerous password system from digital identity. We now protect the digital identity of our clients by offering the safer combinations of ‘physical tokens and biometrics’ instead of the dangerous combinations of ‘passwords’, ‘physical tokens’ and ‘biometrics’.

Biometrics, when used as an authenticator in cyber space, needs to be deployed in ‘multi-entrance’ method with a password/PIN as a fallback measure against false rejection. We now offer the password/PIN-dependent biometrics that provides better security than the password¬-alone authentication. Our proposition is viewed as valid where they do not ask the definition of ‘better’ or for whom it is ‘better’.
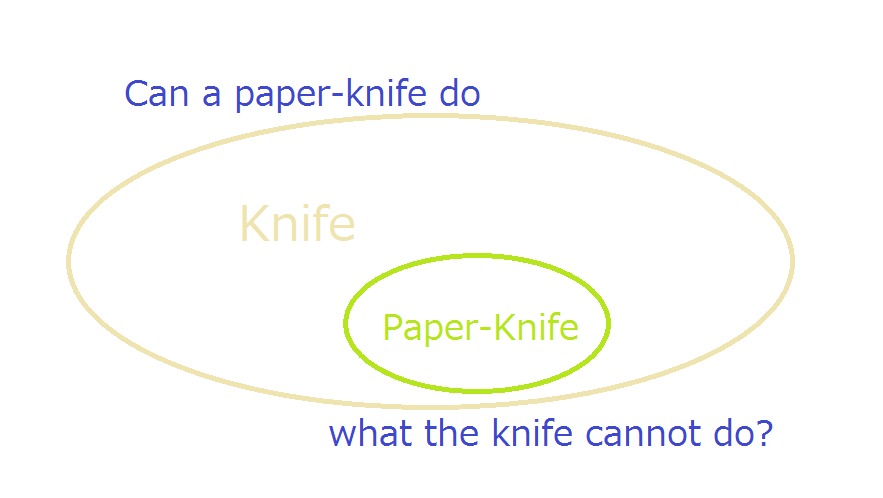
A paper knife (specific/subordinate concept) belongs to the knife (general/superordinate concept). Therefore, a paper knife must be able to perform what the knife is unable to perform.
A PIN, which is a weak form of numbers-only password, belongs to the password. A PIN (specific/subordinate) must be able to offer the high level security that the password (general/superordinate) is unable to offer, possibly in a cyber version of Alice’s Wonderland.
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
Haven’t the biometrics promoters built a huge sandcastle?
Biometrics is said to be growing to be a gigantic business as reported here - Biometrics research notes: banking, systems, Asian retail and smart tickets - https://www.biometricupdate.com/201910/biometrics-research-notes-banking-systems-asian-retail-and-smart-tickets
It reads "Biometrics systems will generate over $65B by 2024, according to new research, with growth in different areas for different regions. Signs are also positive for the industry in banking and securities, Asian retail, and smart ticketing, with significant investments anticipated in each."
The figure of $65 billion is really mind-boggling even if it is bloated 10 times! Then, it should be extremely exciting to imagine what will happen when the myths of biometrics as examined above get debunked in front of the public and the gigantic castle of biometrics proves to have actually been a sandcastle. We might well be watching a huge vacuum generated where there was the gigantic sandcastle.
This false sense of security has only been benefiting criminals, hasn’t it?
As examined above, biometrics has continuously contributed to providing a favorable environment to criminals, not to citizens, for nearly two decades and the public has been misled to believe that biometrics has provided better security for citizens. This false sense of security might well keep causing huge damages on our societal life for many more years unless somebody speaks out articulately.
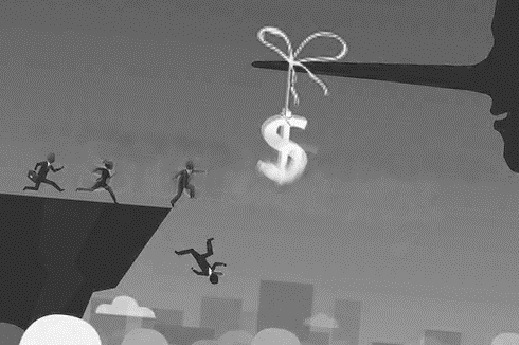
Over several years we have repeatedly made clear that biometrics brings down security to the level lower than a password-only authentication where it is used together with a password in a ‘multi-entrance’ deployment, as against a “multi-layer” deployment.
We have received not a single logical or evidence-based refutation, which led us to suspect that the biometrics guys love a one-way propaganda but hate the exchange of opinions.
They might be prepared to allow people to debate on ‘spoofing’ and ‘data leak’, because they could counter these debates by talking about the eternal endeavor of improving technologies. But it looks like they are aware they cannot afford to be involved in the discussion on the negative security effect of biometrics used with a 'fallback password’ required against false rejection/non-match, presumably because there is absolutely no way of eliminating the presence of trade-off relation between false match/acceptance and false non-match/rejection due to the nature of the body features inherent in living animals.
In other words, it looks as though they are afraid that, should they publicly admit the necessity and actual presence of 'fallback measure', a default password/pincode in most cases, the very foundation of their decades-long allegation of “Biometrics brings better security than passwords” would evaporate right away.
As such we are led to suspect that all that the biometrics guys can do is turn a blind eye, cover their ear, close their mouth and keep earning as much quick money as possible before their 'business model' collapses.
Incidentally, we are also very worried to have noticed that biometrics data is seldom publicized in a logical and scientific manner.
Quite a few biometrics vendors publicize a part of a fact and do not disclose the other part of the fact, for instance, publicizing a nicely low false match/acceptance rate without saying anything about the corresponding false non-match/rejection rate, which could be alarmingly high, but remains unknown to the public.
Subsequently, this phenomenon comes with their silence on the need and presence of a fallback password/pincode against the false non-match/rejection, which brings down security to the level lower than password/pincode-only authentication, as repeatedly made clear in this article.
Moreover, we could add that unsubstantiated theoretical data is often presented as if it were the objective empirical data.
Hey, Biometrics Guys! Get Provoked!
By ‘biometrics guys,’ we mean not just the biometrics vendors but those officials, professionals, researchers, consultants, journalists, etc. who have gained a lot from this dubious way of doing business.
Biometrics Guys! At the early days, you were probably just ignorant of the security-lowering effect of biometrics used with a fallback password, presumably because you were indifferent to and unaware of the opposite security effect of two authenticators used together in a security-enhancing 'multi-layer' deployment and in a security-lowering 'multi-entrance' deployment.

Biometrics Guys! Should you be confident that we are mistaken somewhere in this article, you would be welcomed to refute specifically where you reckon we are wrong.
Conclusion
The password is insufficient, but not harmful.
Biometrics is harmful, and not sufficient.
Attempting to make quick money by spreading a false sense of security is ethically dubious and practically suicidal.
< Related Article >
Proposition on How to Build Sustainable Digital Identity Platform
#identity #authentication #password #security #biometrics #ethic #privacy #democracy #finance #FDATAsummit2019
Hitoshi Kokumaiの記事
ブログを見る
Today's topic is BBC's “Facebook to end use of facial recognition software” · https://www.bbc.com/n ...

https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...
We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password sys ...
この職種に興味がある方はこちら
-

レディース販売
次の場所にあります: Whatjobs JP C2 - 6日前
インポート販売スタッフ/表参道店/LX/138613 Tokyo, 日本**インポート販売スタッフ/表参道店/LX/138613**: · レディース販売 · 【時給1650円+交通費全額支給】制服あり レディースアパレル 販売スタッフ 表参道店(日払い可・交通費全額支給) · - 派遣社員 · - 短期・単発OK · - 週3~4日OK · - 週5日以上 · - 土日のみOK · - シフト制勤務 · - 駅チカ・駅ナカ · - オープニングスタッフ · - 制服貸与 · - 髪型自由 · - 服装自由 · - 社内割引あり · - 社員登用あり · - 交通費支給 · - 日払いOK · - 高収入 · - 未経験者歓 ...
-

介護支援専門員
次の場所にあります: Talent JP C2 - 2日前
公開範囲1.等を含む求人情報を公開する Gonohe, 日本 フルタイム仕事内容 · ・在宅利用者のケアプラン作成業務。 · ・認定調査業務。 · ・配食サービス配達支援業務。3~4回/月 · (在宅高齢者への給食の配達作業) · ・町委託事業支援業務。 1~2回/月 雇用形態 正社員 派遣・請負等 就業形態 派遣・請負ではない 雇用期間 雇用期間の定めなし 就業場所 就業場所 事業所所在地と同じ 〒 青森県三戸郡五戸町字姥堤34番1 受動喫煙対策 あり(屋内禁煙) マイカー通勤 マイカー通勤 可 駐車場の有無 あり 転勤の可能性 転 ...
-

塾講師 アルバイト 個別指導
次の場所にあります: beBee S2 JP - 1週間前
株式会社さなる(佐鳴予備校 個別指導部門 千種本部校) 名古屋市千種区, 日本 パートタイム雇用形態 · アルバイト · 職種・指導形態 · 個別指導 · 給与 · 1授業60分1,320円 · ※送迎時間・事務時間帯は時給1030円 · 最寄駅 · 砂田橋駅より徒歩12分 · 砂田橋駅より 徒歩 12分 · 待遇 · 交通費込 · 研修制度充実 · 仕事内容 · 2名の生徒に対して、学習指導 · 複数勤務地あり。ご応募後のお電話にてご相談下さい。 · ==応募後のご連絡について== · ご応募いただいた方には当社からメールまたはお電話にてご連絡を差し上げます。最短でご対応しておりますが、応募時にご指定いただいた「連絡希望日時」に添えない場合 ...
コメント