Seemingly Fatal Drawbacks of Pictorial Password – Shoulder Surfing & Low Entropy

We have been advocating Expanded Password System that accepts images as well as texts from 2001. We have since kept hearing our proposition blamed for two major ‘drawbacks’ of using images – Shoulder Surfing and Low Entropy. So many people are still misguided to take it for granted as if it were the case.
The fact is that threats of shoulder surfing can be mitigated with ease by some simple techniques - images to get shrunk prior to tapping, texts allocated to images for quiet typing and so on at the end of developers, with the simplest solution being just looking around you before tapping the images at the end of users. How can it be a fatal drawback?
Another seemingly serious problem of low entropy can be eliminated at the end of developers without giving any extra burden on users.
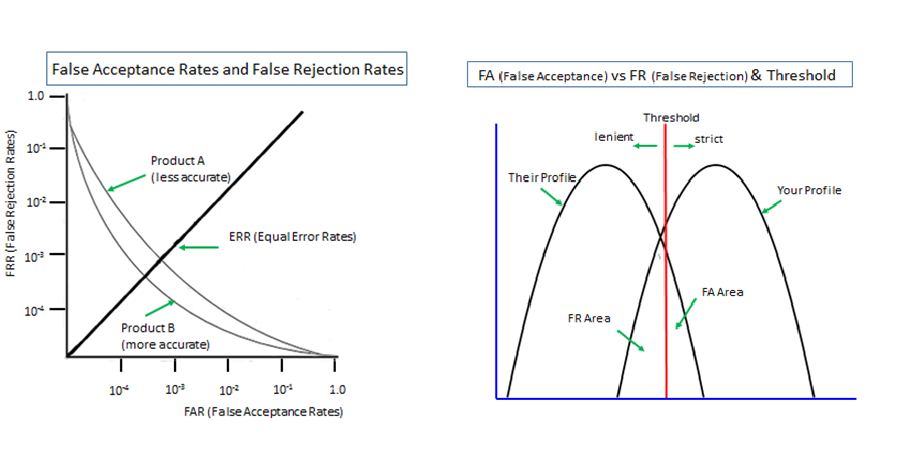
With Expanded Password System, each image or character is presented by the image identifier data which can be of any length. Assume that your password is “CBA123” and that the image ‘C’ is identified as X4s& eI0w, and so on.
When you input CBA123, the authentication data that the server receives is not the easy-to-break“CBA123”, but something like “X4s&eI0wdoex7RVb%9Ub3mJvk…………..” which could be automatically altered periodically or at each access where desired, all without involving users.
Passwords of sufficient entropy, if properly hashed, can stand fierce brute force attacks. How can it be a fatal drawback?
PS
As for amplifying the entropy on the network, we could think about a very simple case as a reference.
You have two passwords - one that you can easily recall and the other that is too long for you to recall and needs to be stored on a paper or your device. You recall the first password and put it at the front or end of the second password before sending it off.
The authentication server obtains its hashed value and get it matched with the stored hash value. This hashed value has a very high entropy unless the hash program is compromised. Our proposition is not too far away in principle from this simple case.
Incidentally, the idea of combining a remembered password and a memo with a password on it could be viewed as an improvised 2-factor authentication that everyone can deploy right away at no cost for much better security than now.
#identity #authentication #password #security #safety #biometrics #ethic #privacy #civilrights #democracy
Hitoshi Kokumaiの記事
ブログを見る
https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...

Another topic for today is “Passwordless made simple with user empowerment” · https://www.securitym ...
関連プロフェッショナル
この職種に興味がある方はこちら
-

美容師/美容師(スタイリスト)
次の場所にあります: beBee S2 JP - 4日前
Primary(プライマリー) 横浜市港南区, 日本 業務委託更新日: · 【業務内容】ヘアサロンにおけるサロンワーク業務全般 · 【雇用形態】 業務委託 · 【勤務地】「上大岡駅」東口より徒歩10秒/地下鉄「上大岡駅」より徒歩3分のヘアサロン · 【給与】■完全歩合制 · 新規50%/指名60% · ※材料費として10%自己負担 · 【試用期間中給与】変動なし · 【PR】 · 【休日】自由出勤 · 【店長歴:1~2年】 · 【店長からのコメント】スタッフ同士の仲が良く、笑顔が絶えない職場です · 『新しい環境に馴染めるのかな...』と不安を感じている方も安心してくださいね♪ · ◎美容が大好きな方 · ◎お客 ...
-

未経験歓迎★キャリアアドバイザー◎残業5h/語学力を活かせる環境です
次の場所にあります: beBee S2 JP - 2日前
ジップラス(株) 東京都, 日本多言語の運転免許情報サイトを運営する当社で,日本での就労に向けた外国籍の求職者サポート及びその他免許取得に関する業務をお任せします。※企業側営業担当(RA)は他社員が担当します。 · 【詳細】2023年に許認可を取得し、企業紹介を行っております。2024年度から本格稼働させるため、今回入社される方には求職者の新規獲得やマーケティング、相談いただいた求職者へのヒアリングを行い、就労サポートしていく仕事です。 · 【その他】■合宿免許受付業務 ■外国免許の切替における翻訳業務 ■その他付随する業務 ...
-

看護師
次の場所にあります: beBee S2 JP - 2日前
こもれび保育園 川崎梶が谷園 川崎市高津区, 日本 TEMPORARY【こもれび保育園 川崎梶が谷園 求人のポイント】 · ◆東急田園都市線 梶が谷駅から徒歩で12分 · JR南武線 津田山駅から徒歩で12分 · 東急田園都市線 溝の口駅から徒歩で17分 · ◆月給 250,000円 ~ · ◆賞与年2回2ヶ月 · ◆園児定員:30名(0~2歳) · ◆即日勤務OK · ◆認可保育園の看護師 · ----- · 勤務地 · ----- · 神奈川県川崎市高津区下作延4-27-1 · ----- · 最寄り駅 · ----- · 東急田園都市線梶が谷駅 徒歩12分JR南武線 徒歩12分 · ----- · 園名 · ---- ...
コメント
Debesh Choudhury
4年前 #1