Robust 2-Channel Authentication
2 is larger than 1, but not necessarily stronger than 1.
https://www.theregister.com/2020/07/20/twitter_security_update_hackers_broke_2fa/
By bringing in the concept of Expanded Password System, we are able to protect important accounts more reliably than conventional 2-factor/step authentications as outlined here – “AdvancedPersistent Threats in Digital Identity”
This is not a hypothesis. It has been quietly but effectively deployed since 2014 for a security-centric corporate network by 1,200 employees.
Needless to say, asymmetric cryptography could be additionally incorporated for yet higher security where needed.
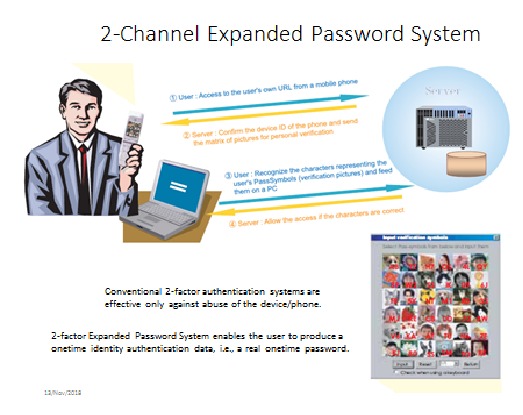
We are confident that we could make significant contributions to mitigating these 3 problems of
preventing the compromise of an OTP token from affecting the overall security of 2F authentication,
preventing the OTP token from getting compromised in the first place
and
preventing the inside jobs.
......................................................................................................................
Expanded Password System, however solid the theory is, would be vulnerable to attacks when it is poorly implemented.
Very fortunately, our first client in Japan who adopted Expanded Password System for 140,000 shoppers (designed for one million users) was extremely demanding about the implementation. We had to satisfy them and actually satisfied them with the solid implementation. Another major client is Japanese army. We naturally had to be very confident about the good implementation.
For both theory and implementation, we owe a lot to Emeritus Prof. Hideki Imai, who was the chairperson of Japan’s CRYPTREC and also a cryptography advisor to the defense forces when we first met in 2001. He pushed my back to move ahead confidently with promotion of Expanded Password System, and helped me a lot with several joint research programs until he retired from Tokyo University. It is from him that I came to know about the likes of Elliptic Curve Cryptography.
Expanded Password System has thus been strongly disciplined and hardened in both theory and implementation.
Hitoshi Kokumai の記事
ブログを見る
https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...

The quantum computer held in a bad guy’s hand is indeed a big threat. So is the artificial intellige ...

Another topic for today is “Passwordless made simple with user empowerment” · https://www.securitym ...


コメント