Detection of Phishing by Episodic Image Memory

In February 2021 global media were in an uproar over this horrifying news - “Hacker tries to poison water supply of Florida city” https://www.bbc.com/news/world-us-canada-55989843
We know that many of the attackers get a back door opened to take over the systems. Probably around the top of the list of weapons for opening the backdoor is compromising the passwords of the staff of target organizations. ‘Phishing’ is known to be particularly effective in it.
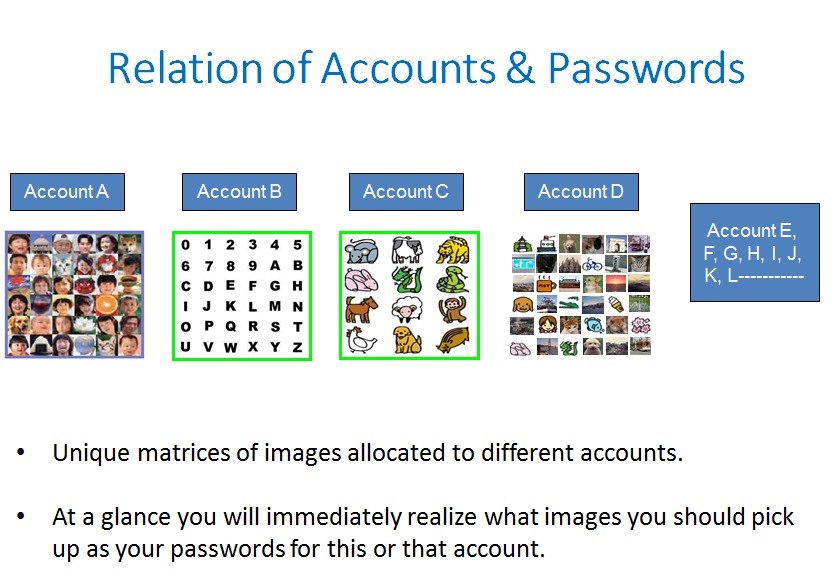
The nasty threats of phishing attacks can be detected and thwarted by a simple tweak of the log-in process with a wise use of our episodic image memory; enable the user to register an image of their own (not shared on SNS) as a credential of the genuine log-in server
When the genuine service desk sends an email to a user, for instance, to ask them to feed their log-in password, the genuine log-in page should be able to show the user’s image - along with dozens of other images. If the user is shown a log-in page that does not show any image that the user can recognize right away, it would be suspected to be a fake log-in page – Beware!
The image to register as a credential of the genuine log-in page should desirably be of episodic memory. We announced this method 18 years ago.
![“Expanded Password System
Bans & Only I can select all of
BL] them correctly
Broader choices with both images and characters accepted
i
Easy 10 manage reletons between accounts and corresponding passwords.
&
Torturous login is hstory. Login is now comfortable, relaxing and heaing
SRO
250
8](https://contents.bebee.com/users/id/13855668/article/detection-of-phishing-by-episodic-image-memory/911f1054.png)
Have you taken note that we wrote “show the user’s image ALONG WITH DOZENS OF OTHER IMAGES” in the above? This element plays a crucial role in our scheme.
A would-be phisher can easily copy the log-in screen and show it to a target user whose User ID is known. But the phisher does not know which image was registered by the user as the credential of the genuine log-in server as against the other images, whereas both the user and the genuine log-in server know which one was registered.
We ask the user to pick up the registered image and also several other meaningless images in a random sequence; The outcome will be that the genuine log-in server will know that the user has selected the registered image in the choice, while a fake log-in server will not know it,
If the user is given a password box when the choice does not include the registered image, the user would know right away that it is a fake and proper actions would be taken. The phishing process will have to stop there. Copying the genuine log-in page would thus take the phisher nowhere.
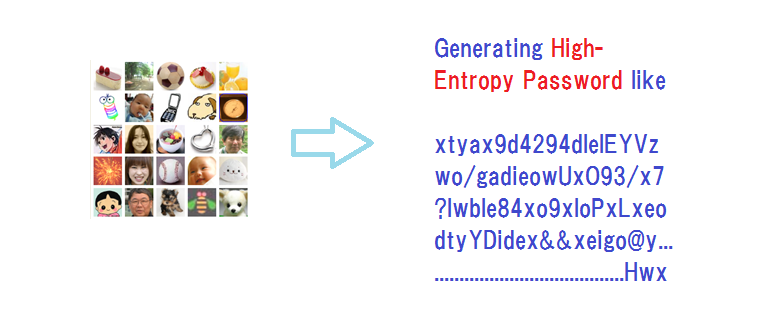
After this screening of fake log-in servers, the user will be asked to go through the authentication by a password, desirably by Expanded Password System (EPS) where it is available. EPS comes without the likes of a password box.
Key References
Digital Identity for Global Citizens
What We Know for Certain about Authentication Factors
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Additional References
Account Recovery with Expanded Password System
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Negative Security Effect of Biometrics Deployed in Cyberspace
Removal of Passwords and Its Security Effect
Update: Questions and Answers - Expanded Password System and Related Issues (30/June/2020)

Hitoshi Kokumaiの記事
ブログを見る
Today's topic is this report - “How blockchain technology can create secure digital identities” · h ...
We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password sys ...

Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...
この職種に興味がある方はこちら
-

相談支援専門員
次の場所にあります: Whatjobs JP C2 - 1週間前
社会福祉法人うぐいす会 千葉市 高田町, 日本【職種名】 · 【相談支援専門員/週3日~・1日4h~勤務OK】無資格・未経験歓迎/ママ世代活躍中 · **仕事内容**: · ――――――――ポイント―――――――― · 〇経験者歓迎 · 資格や今までの経験を活かせるので、 · すぐに活躍することができます · 〇週2日~/4h~可 · ライフスタイルに合わせて働けます · 子育てとの両立や扶養内勤務にもピッタリ · 〇女性スタッフ活躍中 · 女性スタッフの頑張りを後押しする · 待遇や福利厚生があります · 子育て中の社員も活躍中で、 · 急なシフト変更などにも柔軟に対応 · ――――――――――― ...
-

研修所内食堂のホール 配膳
次の場所にあります: Whatjobs JP C2 - 4日前
グリーンホスピタリティフードサービス株式会社 横浜市 鶴見区, 日本**研修所内食堂のホール 配膳**: · **大手会社内での社員クラブ勤務のホール勤務です** · - 掛け持ちOKです。夕方から勤務出来る方募集です · **募集要項**: · **仕事内容** · - 簡単な調理作業 · - 盛付け、片づけ、食器洗浄**掲載企業名** · - グリーンホスピタリティフードサービス株式会社**勤務地** · - 神奈川県 横浜市鶴見区弁天町2番地 AGCモノづくり研修センター**交通アクセス** · - 鶴見線 弁天町駅 徒歩5分**雇用形態** · - アルバイト・パート**給与** · 時給1,112円〜 · 時給 ...
-

塾講師バイト・社会人限定・集団指導
次の場所にあります: Whatjobs JP C2 - 6日前
四谷大塚 渋谷校舎 Tokyo, 日本**アピールポイント**: · 「予習シリーズ」経験者歓迎 教員志望・指導経験ある方お待ちしてます未経験も可 · 本求人から申し込みいただけた場合、採用お祝い金10000円差し上げています。詳しくは応募先をご確認ください。 · **給与(時給)**: · 3000円 · 授業時間に対して時給3,000円です。 · 授業時間以外の業務に対しては時給1,120円となります。 · 例えば面談や父母会、テスト監督などの業務が該当します。 · 研修期間中は時給1,120円です。 · **仕事内容**: · - 小学生向け集団授業 · 担当する学年により仕事内容が異 ...
コメント