Availability-First Approach

People in identity management appear to be busy discussing 'Security-First Approach’ and ‘Convenience-First Approach'. We would like to say ‘Wait a minute! Those discussions could be valid only where citizens are given a means to get themselves somehow authenticated in the first place. Where it is not the case, there would be no ‘Security-First’ nor ‘Convenience-First'.
We believe that it is the obligation of democratic societies to provide citizens with identity authentication measures that are practicable in emergencies as well as in everyday life.
- Can we presume that no citizens trapped in emergencies would ever lose any cards?
- Can we presume that no citizens trapped in emergencies would ever be injured?
- Can we presume that every citizen trapped in emergencies would ever be settled and calm?
We could consider ‘Availability-First Model' as a subject to be considered before further discussing ‘Security-First’ and ‘Convenience-First'. It could be broken into three sub-models as follows.
At the top layer should there be a sub-model that is practicable when we have lost the identity card and the likes.
‘Deployment of a secret credential’ and ‘Deployment of biometrics with a fallback secret credential’ would suffice. (It must be noted that security of the latter is lower than the former because the biometrics and a fallback secret credential must be used together in a security-lowering ‘multi-entrance’ deployment, while convenience of the latter is generally better than the former.)
Beneath it, there should be a sub-model that is practicable when we possess no physical certificate and are injured.
We can rely on the secret credential.
At the bottom layer, there should be a sub-model that is practicable when we are naked, injured and panicked.
We need to rely on the deployment of secret credentials that can stand panic. We are of the view that making use of our autobiographic memory, especially episodic image memory, would make it feasible.
We will be able to offer 'Image-to-Text Converter cum Entropy Amplifier’ to citizens when Expanded Password System that we advocate becomes readily available to all the citizens. Install the converter software on the authentication server and the citizens who are naked, injured and panicked will be able to get themselves authenticated with little friction.
What is practicable in an extreme environment can be practiced in everyday environment, though the reverse is not true. Such an authentication system that copes with the panicked citizens can be operated for all the everyday applications, too, as a stand-alone authenticator, as a factor of multi-factor schemes and as the master password of ID federation schemes.
< Related Article >Proposition on How to Build Sustainable Digital Identity Platform
Hitoshi Kokumai の記事
ブログを見る
I take up this new report today - “Researchers Defeated Advanced Facial Recognition Tech Using Makeu ...
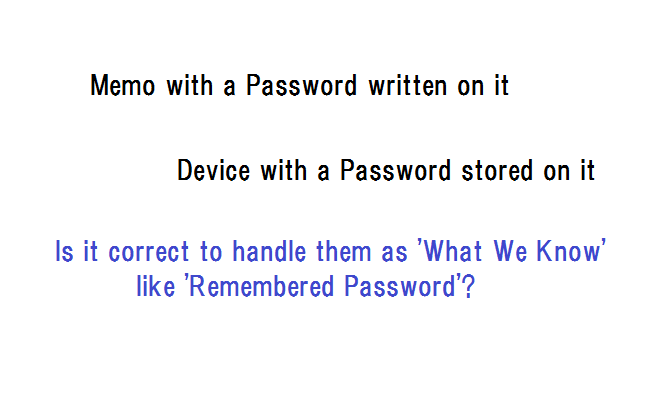
I got interested in this article -on the password problem · “Tech Q&A” · https://www.unionleader.c ...

I would like to take up this somewhat puzzling report - “Google advises passwords are good, spear ph ...
これらの仕事に興味があるかもしれない
-
Quality Assurance Professional / 4을웝의는주재하 · きた QA高MS · QMS Business Reviewer & Approver BATCH Document Review & Release · Deviation, Change Request, Customer Complaint Evaluation and Approval · Patient and Product Potential Risk Assessment and Proposal of Countermeasures · Dail ...
Koriyama-Fukushima Metropolitan Area1ヶ月前
-
MR / Senior MR (//) DIAETES & OBECITY / / · Category: Sales · Location: Chiyoda, Tokyo, JP · ...
東京都 千代田区1ヶ月前
-
· Job Title: Quality Assurance Professional / 品質保証担当者 · Department: 郡山工場品質保証部 · Location: 福島県、日本 · Teaser · 郡山工場では社員の労働環境をより良いものにするため、EHS(Environment, Health & Safety/環境・安全衛生)の充実を心がけております。例としては、地盤の強い敷地を選び建てられていること、また、施設としては社員食堂、ジム、マッサージチェアの設置などがあり、本ポジションにおいてはFlex time制度(コアタイムなし ...
Japan1日前


コメント