3-Factor Configuration Weaker than 2-Factor Authentication
Assuming that a mobile device sends out a private key (or a digital certificate signed by the private key) upon verification of the user by 'Either a biometrics Or a fallback password/PIN' to the authentication server where the corresponding public key is stored, we count 3 factors in this scheme- what you have, what your body features are and what you know/remember.
Is this scheme
1. a 3-factor authentication?
2. a 2-factor authentication?
3. neither a 3-factor nor a 2-factor authentication?
Which of (1), (2) and (3) do you think is the correct answer?
The above was the question I presented in my earlier article. Here is our answer: (3) is correct, i.e., it is neither a 3-factor nor a 2-factor authentication. It actually is a ‘below-2’-factor authentication because two of the 3 factors were assumed to be deployed in ‘Multi-Entrance’ (EitherOr/in-parallel) method, not in ‘Multi-Layer’ (BothAnd/in-series) method, in my question.
Logic dictates that, when 2 authentication factors are deployed in ‘Multi-Layer’ method, security goes up while convenience goes down. On the other hand, security goes down while convenience goes up when deployed in ‘Multi-Entrance’ method as demonstrated in this video - https://youtu.be/wuhB5vxKYlg
In cyberspace biometrics is usually deployed in ‘Multi-Entrance’ method with a password/PIN as a fallback measure against false rejection. Saying “Biometrics is more convenient than Password” is OK, while “Biometrics is more secure than Password” is simply false.
However inconvenient and embarrassing to the people who have been talking otherwise, this is the fact.
Hitoshi Kokumai の記事
ブログを見る
Our password headache may well be the consequence of these dual causes - · ‘Use of Impracticable Pas ...

Taken up today is this TechRepublic report on voice print as a new password - https://www.techrepubl ...
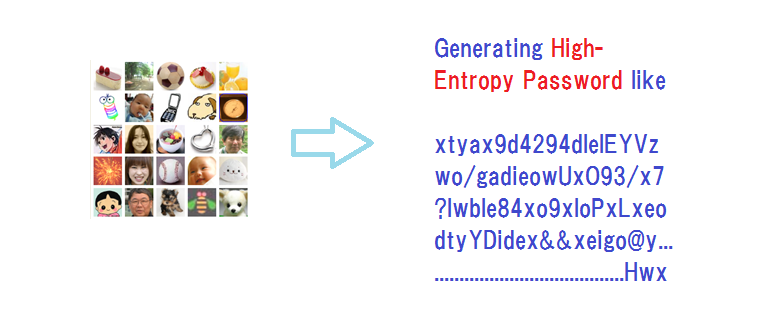
We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password sys ...


コメント