Phishing Attack and Episodic Memory
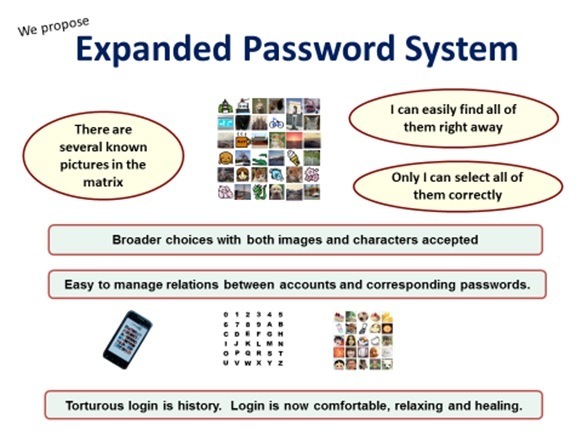
![“Expanded Password System
Bans & Only I can select all of
BL] them correctly
Broader choices with both images and characters accepted
i
Easy 10 manage reletons between accounts and corresponding passwords.
&
Torturous login is hstory. Login is now comfortable, relaxing and heaing
SRO
250
8](https://contents.bebee.com/users/id/13855668/article/phishing-attack-and-episodic-memory/8156c83c.png)
"Hacker tries to poison water supply of Florida city" https://www.bbc.com/news/world-us-canada-55989843
Horrifying report indeed!
We hear that many of the attackers get a back door opened to take over the systems. Probably around the top of the list of weapons for opening the backdoor is compromising the passwords of the staff of target organizations. ‘Phishing’ is known to be particularly effective in it.
I wish to see more people recognize this - Our own episodic memory will help us to mitigate the nasty threat of phishing.
It was discussed in these recent posts -
“Detection ofFake Log-In Page”
“Sequel - Detection of Fake Log-In Page”

Key References
Digital Identity for Global Citizens
What We Know for Certain about Authentication Factors
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Additional References
Account Recovery with Expanded Password System
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Negative Security Effect of Biometrics Deployed in Cyberspace
Removal of Passwords and Its Security Effect
Update: Questions and Answers - Expanded Password System and Related Issues (30/June/2020)
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
< Media Articles Published in 2020 >
Digital Identity – Anything Used Correctly Is Useful https://www.valuewalk.com/2020/05/digital-identity-biometrics-use/
‘Easy-to-Remember’ is one thing ‘Hard-to-Forget’ is another https://www.paymentsjournal.com/easy-to-remember-is-one-thing-hard-to-forget-is-another/
Identity Assurance And Teleworking In Pandemic https://www.informationsecuritybuzz.com/articles/identity-assurance-and
Hitoshi Kokumai の記事
ブログを見る
I got interested in this article -on the password problem · “Tech Q&A” · https://www.unionleader.c ...

https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...

I take up this report today - “Facebook's metaverse plans labelled as 'dystopian' and 'a bad idea'” ...


コメント