Expanded Password System to Complement FIDO

2 is larger than 1 but is not necessarily stronger than 1, as two children could be overwhelmed by a grown-up.
For a two-factor authentication to be really reliable, each factor should be reasonably secure and usable enough.
On the other hand, ‘password-less’ authentication, however attractive it might sound, would only benefit bad guys as examined in the link page.
https://www.linkedin.com/pulse/removal-passwords-its-security-effect-hitoshi-kokumai/
People who offer a token as 'a factor' of two factor authentication schemes could all be viewed as our potential down-stream partners. Among them are the people who offer FIDO2-compatible solutions.
Put together, we could come up with the two-factor authentications that are much more reliable than otherwise.
.............................................................................................................
What does not exist will never be stolen
Removing what can be stolen from the picture can indeed ensure that what can be stolen will never be stolen and abused.
Removing the password from digital identity can obviously ensure that the password will never be stolen and abused. Then, exactly by the same logic, removing the cryptographic-enabled physical token can also ensure that the cryptographic-enabled physical token will never be stolen and abused.
This cartoon produced 15 years ago will hopefully help to unravel this seemingly complicated but actually simple problem.
I am very curious to know what the promoters of 'token-based password-less authentication' have to say.
What you ignore does not exist
Inconvenient reality?
Ignore it and it does not exist.
Two factors used together in a security-lowering ‘multi-entrance’ deployment and the two factors used together in a security-enhancing ‘multi-layer’ deployment have exactly the opposite security effects?
Ignore it and it does not exist. You will have the security-enhancing biometrics used with a default/fallback password in a security-lowering ‘multi-entrance’ deployment.
Being insufficient is different to being harmful?
Ignore it and it does not exist. You will see a password-removed authentication that is more secure than a password authentication. By the same logic, you will also see a token-removed authentication that is more secure than a token-based authentication.
PIN is no more than a weak form of numbers-only password?
Ignore it and it does not exist. You will have a ‘PIN-based Password-less authentication’.
Hitoshi Kokumai の記事
ブログを見る
Taken up today is this TechRepublic report on voice print as a new password - https://www.techrepubl ...

Some friends directed my attention to this news report - · “Biometric auth bypassed using fingerpri ...
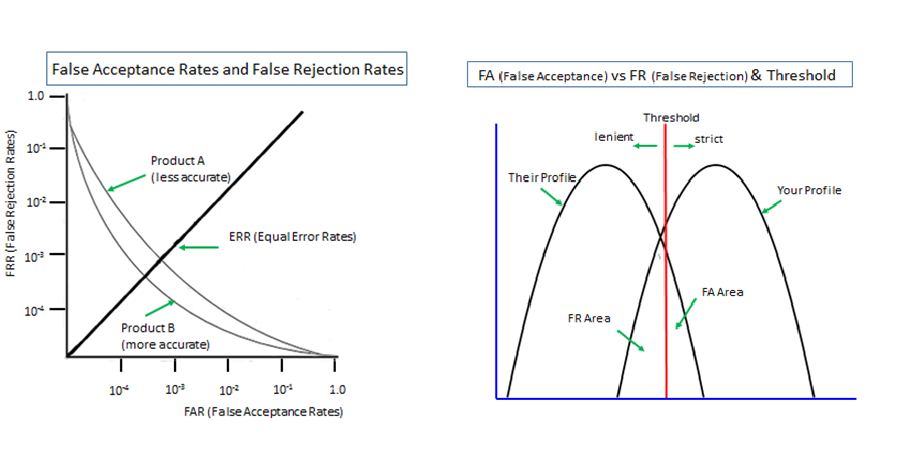
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...


コメント