Expanded Password System: ‘Image-to-Code Converter’
In my earlier post “"Global HQRegistered in UK", I mentioned that people engaged in identity management or ‘deployment of authenticators’ could all be the down-stream partners for Expanded Password System (EPS).
Are you working in the fields of ID federations, two/multi-factor authentications, cryptographic solutions and other areas somehow related to identity management?
Then you might be interested to hear thatthe core of EPS is designed to convert images to high-entropy codes, which work as very long passwords and also as the seeds of symmetric or asymmetric cryptographic keys.
You will please keep watching us and wait for the completion of our 'Image-to-Code Converter' software module that you will be able to plug into your solutions.
Or, you could consider being more proactive and helping us accelerate the process in some way or other for making your EPS-powered solutions available to your customers speedily.
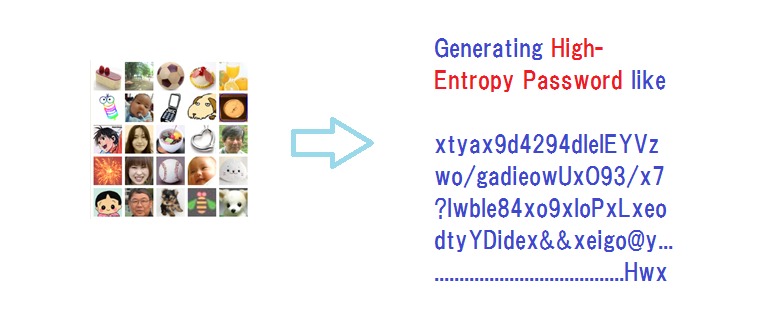
Theory and Implementation
Expanded Password System, however solid the theory is, would be vulnerable to attacks when it is poorly implemented.
Very fortunately, our first client in Japan who adopted Expanded Password System for 140,000 shoppers (designed for one million users) was extremely demanding about the good implementation. We had to satisfy them and actually satisfied them with the very solid implementation. The latest client is Japan's Self-Defense Ground Forces (aka Army). We naturally had to be very confident about the good implementation.
What enabled us to design the good implementation is the guidance we were given by Emeritus Prof. Hideki Imai of Tokyo University, who was the chairperson of Japan’s CRYPTREC when we first met in 2001. He pushed my back to move ahead confidently with promotion of Expanded Password System, and helped me a lot with several joint research programs until he retired from Tokyo University.
He emphasized to me repeatedly how critical it is to design the good implementation. First of all, hashing the credential data is an absolute must whether on line or offline. It is also from him that I came to know about Deffie-Hellman Key Exchange, Elliptic Curve Cryptography and so on.
As such, we are fully certain that not only the solid theory but also the good implementation is indispensable to have Expanded Password System correctly valued by the security-centric corporations and organizations wherever we go.
Who Adopted Expanded Password System (EPS) and for What
A telecom company who built a payment system designed for a million online shoppers adopted EPS for accepting ‘Hard-to-Forget’ and yet ‘Hard-to-Break’ credentials and for reducing the helpdesk cost drastically. Actually 140,000 online shoppers enjoyed the no friction login before the payment system was closed in 2008.
An IT corporation who built a security-conscious corporate network adopted EPS-based 2-channel/2-factor authentication accepting ‘Hard-to-Break’ and yet ‘Hard-to-Forget’ credentials. 1,200 employees are still enjoying the good balance of security and usability.-
Japan’s Self-Defense Ground Forces, aka Army, adopted our product for accepting ‘Panic-Proof’ and yet ‘Hard-to-Break’ credentials. The number of licenses has increased more than 10-fold over the 7-year period from 2013 and is set to increase further.
We expect to see similar adoptions in hundreds or thousands of times larger scale once we start the operation in the global market from the quarters in UK.
Cryptography and Expanded Password System
As mentioned earlier, Prof. Hideki Imai pushed my back to move ahead confidently in 2001 when he was the chair of Japan’s CRYPTREC. He repeatedly emphasized to me how critical it is to hash the credential data whether online or offline. It is also from him that I came to know about the topics of Deffie-Hellman Key Exchange, Elliptic Curve Cryptography, etc. Let me talk about the 2002 – 2004 joint research projects we progressed.
Firstly, we tried the methodology of using the high-entropy credential data generated by Expanded Password System (EPS) as the seed of RSA key pair. With the scheme, the user's private key does not physically exist anywhere in the universe, but it can be re-generated on-the-fly out of the images that the user picks up for authentication for each login. It proved to work on the internet. At that time I was told we should look at Elliptic Curve Cryptography in the future as a successor to RSA.
Thereafter, we took up the experiment of incorporating Expanded Password System into PAKE (simplified version developed at Tokyo University).We were able to demonstrate that it worked with no friction in the lab environment.
Both projects were financed by Japan’s government agencies, Unfortunately, however, the officials who received our reports showed no interest in a budget to enable us to expand the experiments further. We might have started these forward-looking projects a bit too early.
< References >
Proposition on How to Build Sustainable Digital Identity Platform
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Negative Security Effect of Biometrics Deployed in Cyberspace
Removal of Passwords and Its Security Effect
Update: Questions and Answers - Expanded Password System and Related Issues (30/June/2020)
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
< Latest Media Articles Published in 2020 Spring>
Digital Identity – Anything Used Correctly Is Useful https://www.valuewalk.com/2020/05/digital-identity-biometrics-use/
‘Easy-to-Remember’ is one thing ‘Hard-to-Forget’ is another https://www.paymentsjournal.com/easy-to-remember-is-one-thing-hard-to-forget-is-another/
Identity Assurance And Teleworking In Pandemic https://www.informationsecuritybuzz.com/articles/identity-assurance-and
Hitoshi Kokumai の記事
ブログを見る
Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...
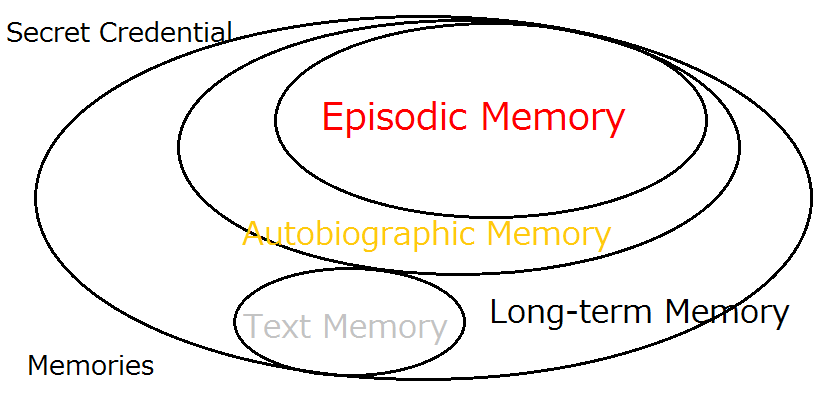
There is actually a valid methodology that enable us to maximize the entropy of the secret credentia ...

I take up this report today - “Facebook's metaverse plans labelled as 'dystopian' and 'a bad idea'” ...


コメント