Who Adopted Expanded Password System and for What
A telecom company who built a payment system designed for a million online shoppers adopted Expanded Password System (EPS) for accepting ‘Hard-to-Forget’ and yet ‘Hard-to-Break’ credentials and for reducing the helpdesk cost drastically. Actually 140,000 online shoppers enjoyed the no friction login before the payment system was closed in 2008.
An IT corporation who built a security-conscious corporate network adopted EPS deployed in 2-channel/2-factor scheme for accepting ‘Very Hard-to-Break’ and yet ‘Hard-to-Forget’ credentials. 1,200 employees are still enjoying the good balance of security and usability.
Japan’s Self-Defense Ground Forces, aka Army, adopted our product for accepting ‘Panic-Proof’ and yet ‘Hard-to-Break’ credentials. The number of licenses has increased more than 10-fold over the 7-year period from 2013 and is set to increase further.
We expect to see similar adoptions in hundreds or thousands of times larger scale once we start the operation in the global market from the headquarters in UK.
![“Expanded Password System
Bans & Only I can select all of
BL] them correctly
Broader choices with both images and characters accepted
i
Easy 10 manage reletons between accounts and corresponding passwords.
&
Torturous login is hstory. Login is now comfortable, relaxing and heaing
SRO
250
8](https://contents.bebee.com/users/id/13855668/article/who-adopted-expanded-password-system-and-for-what/df7e8793.jpg)
Availability-First Approach
People in identity management appear to be busy discussing 'Security-First Approach’ and ‘Convenience-First Approach'. We would like to say ‘Wait a minute! Those discussions could be valid only where citizens are given a means to get themselves somehow authenticated in the first place. Where it is not the case, there would be no ‘Security-First’ nor ‘Convenience-First'.
We believe that it is the obligation of democratic societies to provide citizens with identity authentication measures that are practicable in emergencies as well as in everyday life.
- Can we presume that no citizens trapped in emergencies would ever lose any cards?
- Can we presume that no citizens trapped in emergencies would ever be injured?
- Can we presume that every citizen trapped in emergencies would ever be settled and calm?
We could suggest ‘Availability-First Model' as a subject to be considered before further discussing ‘Security-First’ and ‘Convenience-First'. It could be broken into three sub-models as follows.
At the top layer should there be a sub-model that is practicable when we have lost the identity card and the likes.
- ‘Deployment of a secret credential’ and ‘Deployment of biometrics with a fallback secret credential’ would suffice. (It must be noted that security of the latter is lower than the former because the biometrics and a fallback secret credential must be used together in a security-lowering ‘multi-entrance’ deployment, while convenience of the latter is generally better than the former.)
Beneath it, there should be a sub-model that is practicable when we possess no physical certificate and are injured.
- We can rely on the secret credential.
At the bottom layer, there should be a sub-model that is practicable when we are naked, injured and panicked.
- We need to rely on the deployment of secret credentials that can stand panic. We are of the view that making use of our autobiographic memory, especially episodic image memory, would make it feasible.
We will be able to offer 'Image-to-Text Converter cum Entropy Amplifier’ to citizens when Expanded Password System that we advocate becomes readily available to all the citizens. Install the converter software on the authentication server and the citizens who are naked, injured and panicked will be able to get themselves authenticated with little friction.
What is practicable in an extreme environment can be practiced in everyday environment, though the reverse is not true. Such an authentication system that copes with the panicked citizens can be operated for all the everyday applications, too, as a stand-alone authenticator, as a factor of multi-factor schemes and as the master password of ID federation schemes.
Hitoshi Kokumaiの記事
ブログを見る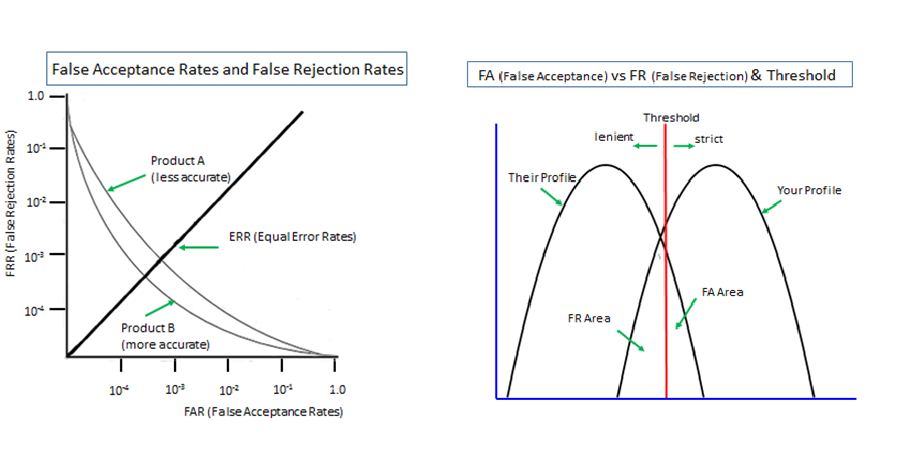
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...

Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...
I got interested in this article -on the password problem · “Tech Q&A” · https://www.unionleader.c ...
この職種に興味がある方はこちら
-

保育士
次の場所にあります: beBee S2 JP - 5日前
さくら上宮保育園 渋谷区, 日本 TEMPORARY【さくら上宮保育園 求人のポイント】 · ◆JR山手線・東急東横線「渋谷駅」徒歩5分 · ◆園児定員:70名(0歳~5歳) · ◆月給202,868円~209,652円(手当含む) · ◆認可保育園の保育士 · ----- · 勤務地 · ----- · 東京都渋谷区桜丘町23-21渋谷区文化総合センター大和田 ロビー階 · ----- · 最寄り駅 · ----- · JR山手線渋谷駅 徒歩5分東急東横線 · 渋谷駅 徒歩5分 · ----- · 園名 · ----- · さくら上宮保育園 · ----- · 施設形態 · ----- · 認可保育園 ...
-
新規輸出事業を担う★商社の海外企画営業ポジションです
次の場所にあります: beBee S2 JP - 1日前
株式会社スタイルワン 東京都, 日本新規事業として中国やアメリカなど海外マーケットに向けた輸出事業をスタートさせるにあたり、販路の新規開拓から輸出貿易まで全工程を担う戦力を増員募集いたします · 【具体的な業務内容】 · ・営業活動 · - 商品の仕入折衝 · - 卸先への商品提案(主にメール、wechat、LINEなどを使用) · - 仕入先/卸先の新規開拓 · - 中国越境EC運営 · ・商品管理業務 · - 受発注、契約管理、売上管理、納品管理、在庫管理 他 · ・顧客対応 · - カタログや書類などの送付、商品(サンプル)送付、電話、メール対応、顧客からの注文受付、在庫の問い合わせ ...
-

看護師/シニア
次の場所にあります: Whatjobs JP C2 - 10時間前
横浜丘の上病院 Yokohama, 日本**医療法人社団緑水会横浜丘の上病院公式求人概要** · **横浜丘の上病院** · ≪シニア雇用促進求人≫時間外ほぼなし&17:00終業◆時給1600円以上★【横浜市戸塚区、東戸塚駅、病院/精神科、看護師(シニア)、日勤パート】 · **職種** · 看護師/シニア · **所在地** · 神奈川県横浜市戸塚区平戸1-20-28 · **給与** · 時給1600円以上 · ※精神科経験がある場合は時給1650円以上 · ※経験・能力により異なる · **求人詳細** · ≪シニア雇用促進求人≫時間外ほぼなし&17:00終業◆時給1600円以上★【横浜 ...

コメント