Two Ways of Deploying Two-Factor Authentication

Using two factors together does not always bring higher security.
Higher security is obtained when two factors are used in ‘multi-layer’ deployment at the sacrifice of convenience, while better convenience is obtained when two factors are used in ‘multi-entrance’ deployment at the sacrifice of security.
We must be careful not to mix up these two ways of deployments that have exactly the opposite security effects lest a serious false sense of security should be created and spread.
------------------------
Quantitative Examination of Multiple Authenticator Deployment
It appears that there are so many security professionals who pay no attention to the exactly opposite effects of 'multi-layer' and 'multi-entrance deployments. ‘Multi-Layer’ is also represented by ‘In-Series’, ‘In-Addition-To’, ‘All/BothAnd’ and ‘Conjunction’ in logic, while ‘Multi-Entrance’ by ‘In-Parallel’, ‘In-Stead-Of’, ‘EitherOr’ and ‘Disjunction’. Let me offer a quantitative examination of multiple authenticators deployed in two different ways.
Vulnerability (attack surface) of an authenticator is generally presented as a figure between 0 and 1. The larger the figure is, the larger the attack surface is, i.e., the more vulnerable. Assume, for instance, as just a thought experiment, that the vulnerability of the PKI-enabled token (x) be 1/10,000 and that of the password (y) be 10 times more vulnerable, say. 1/1,000. When the two are deployed in ‘multi-layer’ method, the total vulnerability (attack surface) is the product of the two, say, (x) and (y) multiplied. The figure of 1/10,000,000 means it is 1,000 times more secure than (x) alone.
On the other hand, when the two are authenticators deployed in ‘multi-entrance’ method, the total vulnerability (attack surface) is obtained by (x) + (y) – (xy), approximately 0.0011. It is about 11 times less secure than (x) alone.
So long as the figures are below 1, whatever figures are given to (x) and (y), deployment of 2 authenticators in ‘multi-layer’ method brings higher security while ‘multi-entrance’ deployment brings lower security. As such ‘multi-layer’ and ‘multi-entrance’ must be distinctly separated when talking about security effects of multiple authenticators.
Remark: Some people may wonder why (xy) is deducted from the sum of (x)+(y).
When (x) and (y) is very small, the (xy) is very close to 0, which we can practically ignore. But we should not ignore it when the figures are considerably large.
Suppose a case that both the two authenticators are deployed in an extremely careless manner, for instance, that the attack surfaces of (x) and (y) reach 70% (0.7) and 60% (0.6) respectively. If simply added the figure would be 130% (1.3). It conflicts with the starting proposition the figures being between 0 and 1.
Imagine a white surface area. Painting 70% of it in black leaves 30% white surface. Painting 60% of the remaining 30% in black will result in 88% black and 12% white surfaces. Painting 60% first in black and then painting 70% of the remaining 40% brings the same result of 88% black and 12% white. So does “(x)+(y)-(xy)”. The overall vulnerability (attack surface) is 0.88 (88%) in this case.
The same calculation applies to biometrics used in cyber space where it has to rely on a fallback password/PIN deployed in ‘multi-entrance’ method against false rejection. You might assume that biometrics deployed with a password/PIN in ‘multi-layer’ method should bring us a very high security. But, very sadly, this scenario never comes true. When rejected by biometrics, what can we do? We will only see that we are unable to login even if we can feed our password/PIN.
< Related Article >
Negative Security Effect of Biometrics Deployed in Cyberspace
Hitoshi Kokumaiの記事
ブログを見る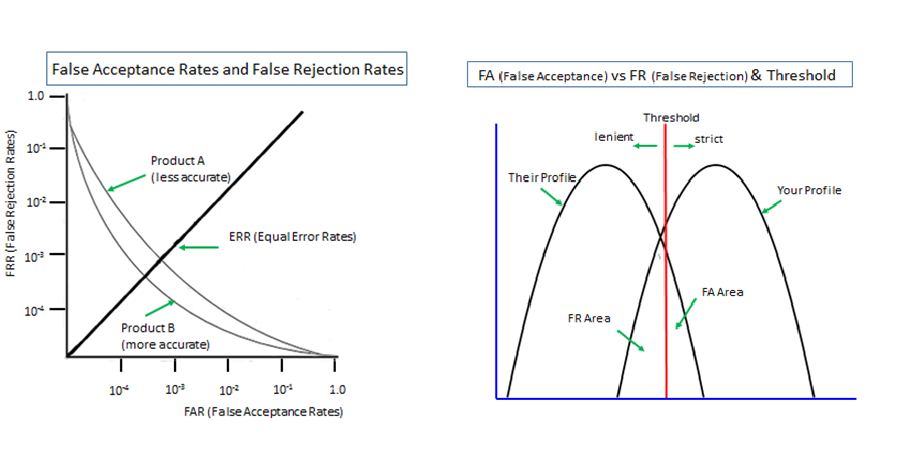
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...

https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...

Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...
この職種に興味がある方はこちら
-
バイクによる配達等【アルバイト・パート/契約社員】
次の場所にあります: Talent JP C2 - 1日前
峡南郵便局 Ichikawamisato, 日本お仕事内容 · ●配達スタッフ● · バイクを使用して、郵便物等の配達をお願いします · ▼未経験・ブランクがある方歓迎▼ · 「免許は持ってるけど、バイクに乗る仕事をしたことがない...」 · 「経験者だけど、ブランクがあるから不安...」 · そんな心配は一切ナシ · わからないこと・不安なことは · 先輩スタッフがしっかりフォローします · 安心してお仕事できますよ♪ · 「ちょっと気になるな...」 · そんな方、お気軽にご応募下さい◎ · 給与時給1,250円 · ※時給(1,250円)には、基本時給(1,000円)とは別に支給する1時間当 ...
-

塾講師 アルバイト 個別指導
次の場所にあります: beBee S2 JP - 6日前
明光義塾 新所沢 所沢市, 日本 パートタイム雇用形態 · アルバイト · 職種・指導形態 · 個別指導 · 給与 · 1コマ95分1,800円〜2,000円 · 研修期間中1700円 · 最寄駅 · 新所沢駅より徒歩3分 · 西武新宿線 新所沢駅東口よりバス通りを直進3分 · 待遇 · 交通費支給 昇給あり · 勤務地 · 埼玉県所沢市松葉町17-14 クリエイトマスミビル4F · ...
-

塾講師 アルバイト 個別指導/事務スタッフ
次の場所にあります: beBee S2 JP - 3時間前
ナビ個別指導学院 東海校 那珂郡東海村, 日本 パートタイム雇用形態 · アルバイト · 職種・指導形態 · 個別指導 · 事務スタッフ · ※個別指導のほか、授業以外の雑務や、自習室の対応をお願いすることがあります。 · 給与 · 1コマ90分1,700円〜2,200円 · 時給で1134~1467円 · 最寄駅 · 東海駅より徒歩4分 · 待遇 · 研修期間中は1コマ(90分)1,450円 · 授業以外の雑務、自習室対応の場合は、時給953円 · 昇給あり 正社員登用あり · 仕事内容 · 自分自身のことを振り返りノウハウを伝えたり、成績UPを一緒に喜んだり · 子供の夢を応援するお仕事とっても「やりがい」 ...

コメント