To Mitigate Insider Threats
Here is a chilling report “Forget yourspace-age IT security systems. It might just take a $1m bribe and a willingemployee to be pwned”
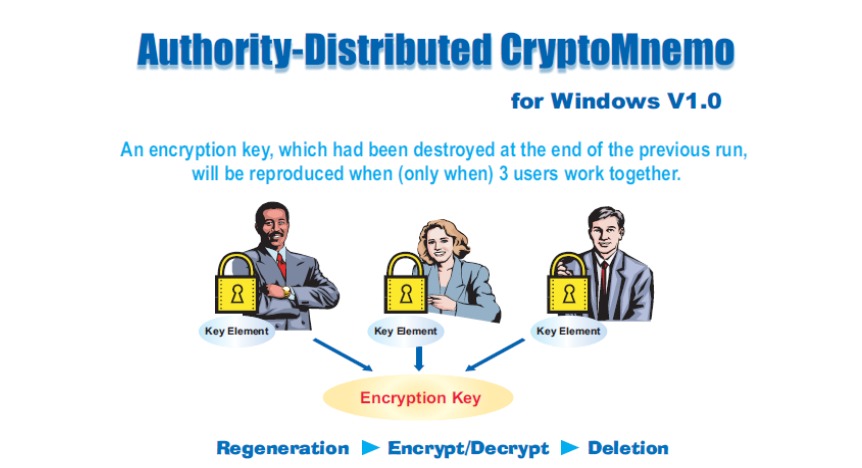
To help mitigate these internal threats, we have our own proposition named Authority-Distributed CryptoMnemo, with which an encryption/decryption key, which had been destroyed at the end of the previous run, will be regenerated on-the-fly when (only when) 3 users work together. The key will be eliminated again when the program is closed.
The CryptoMnemo software was completed in 2005. But we soon ran out of money for putting it on the market and we have since had no resources to bring it back. Now that we have set up our headquarters in UK for the global operations, we are considering its revival with the latest safe coding technologies.
The system can be easily tweaked to regenerate a private key of the public/private key pair instead of a symmetric key.
** The essential point is that we do not rely on 'hard-to-remember' and 'easy-to-evaporate' text passwords but rely on 'hard-to-forget' and ‘panic-proof’ episodic image memory that had solidly fixed deep in our brain for many years as the original seed of the cryptographic keys.
< References >
Image-to-Code Conversion by Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Negative Security Effect of Biometrics Deployed in Cyberspace
Removal of Passwords and Its Security Effect
Update: Questions and Answers - Expanded Password System and Related Issues (30/June/2020)
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
< Latest Media Articles Published in 2020 Spring>
Digital Identity – Anything Used Correctly Is Useful https://www.valuewalk.com/2020/05/digital-identity-biometrics-use/
‘Easy-to-Remember’ is one thing ‘Hard-to-Forget’ is another https://www.paymentsjournal.com/easy-to-remember-is-one-thing-hard-to-forget-is-another/
Identity Assurance And Teleworking In Pandemic https://www.informationsecuritybuzz.com/articles/identity-assurance-and
Hitoshi Kokumaiの記事
ブログを見る
Today's topic is this report - “How blockchain technology can create secure digital identities” · h ...

Another topic for today is “Passwordless made simple with user empowerment” · https://www.securitym ...

https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...
この職種に興味がある方はこちら
-

塾講師 アルバイト 個別指導
次の場所にあります: beBee S2 JP - 1日前
ESOH個伸塾 幕張本郷教室 千葉市花見川区, 日本 パートタイム雇用形態 · アルバイト · 職種・指導形態 · 個別指導 · 【全て1人1人個別に指導する個別指導です】 · 11:2個別・・・先生1人に対して生徒2人の個別指導 · (指導は1人1人個別に教えます) · 21:1個別・・・先生1人に対して生徒1人の個別指導 · 給与 · 1コマ80分2,000円〜2,800円 · ・個別指導 1コマあたり2000円から(経験に応じて考慮します) · 授業以外のお仕事(研修など)には業務給が発生します。 · ≪モデル≫ · ・【例】コマ給1700円、1コマ80分×2コマ出勤した場合2000×2=4000円+交通費 · ...
-

ネイルスタッフ
次の場所にあります: Whatjobs JP C2 - 6日前
cdm 大阪市 住之江区, 日本【職種名】 · 【ネイルスタッフ】北加賀屋エリアで人気のサロンの姉妹店でネイリスト募集♪技術レッスン有◎ · **仕事内容**: · ◇cdm jouerとは · ネイルサロンcdmの姉妹店として「遊び心」をコンセプトとして、自由な発想でデザインを楽しんだり、アートの感性が高い人をターゲットにしたサロンで、入り口には「be playful start here」→ · 遊び心を持ってここから始めようという言葉を刻んでいます。 · cdm jouer から自由にネイルを楽しみ、やりたいことに挑戦できるサロンでありたいと思っています。 · ❏cdm・ホットペ ...
-

児童発達支援管理責任者
次の場所にあります: Whatjobs JP C2 - 2日前
Smm株式会社 和泉市 池田下町, 日本【職種名】 · 【児童発達支援管理責任者/入社定着金50万円】月32万以上未経験OK/賞与あり/チャレンジ歓迎/ · **仕事内容**: · ーポイントー · 〇賞与あり · 頑張りがしっかりと反映され、 · モチベーションを保ちながら働けます · 〇育児サポートあり · 子育て中のスタッフも多数活躍しています · 家庭を持ちながら働いている方も多く、 · 周囲の理解が得られる環境です · 〇未経験・ブランク活躍中 · 保育所、小規模保育園、認定こども園、 · 託児所、児童発達支援(児発)、療育などの · 経験が活かせます · 学童保育、放課後等デイサー ...
コメント