Threat of Biometrics to Security and Its Structure
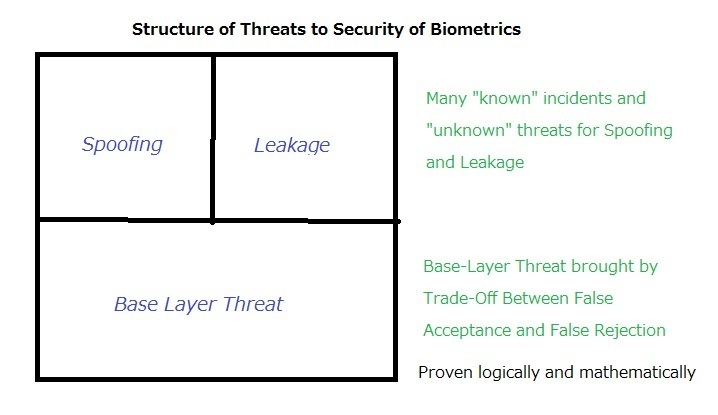
Threats of biometrics to privacy, democracy and humanity are already taken up by quite a few people, but not many people are discussing the threat to security of biometrics and many of them are often carried away by the eye-catching ”known” incidents of spoofing and leakage. Few people pay attention to the base-layer problem solidly inherent in the biometrics technology.
Assume an extremely unlikely scenario that someone comes up with a set of dream solutions by which there can be no spoofing and no leak of biometric data altogether. Even such a 'perfect biometrics' would only provide the level of security lower than a password/pincode-only authentication in cyberspace because biometrics needs to be deployed with a fallback measure (usually default password/pincode) against false rejection (false non-match) in a 'multi-entrance' deployment.
This peculiarity constitutes the base layer of the threat to security of biometrics. On top of this base layer, biometrics gives us additional layers of threats; spoofing and data leakage, which are supposed to haunt us for long in this real world.
By the way, as for the threats of spoofing and leakage, we need to assess both “known” incidents or precedents and “unknown” threats.
Just as the threat of man-made crimes should be assessed differently from the threat of natural disaster, new threats of ever-evolving digital crimes should be assessed differently from the time-honored threat of pre-digital crimes. If we have to wait for an incident or precedent to be “known to us” before we are allowed to discuss the threat, we would never be able to logically and mathematically identify the threat and prevent the identified threat from actually turning into an incident or precedent.
Whether a logical and mathematical reasoning of a potential threat is correct or wrong can only be tested logically and mathematically, not by whether it is known or not, whereas a physical phenomenon, for instance, whether this key fits into that lock or not could be tested physically.
Separately we could assess the threats of biometrics to the security of individual persons as well as that of the overall networks. Attacks on individuals must not be dismissed as a trivial matter.
Mr. A, for instance, is not wealthy so he can be confident that no bad guys would try to attack his accounts for money. He cannot be confident, however, that no bad guys would try to break into his accounts for personal revenge or harassment. He believes he has lived honestly, trying not to harm anyone. But it does not guarantee that he does not get hated. When his biometric data gets leaked, it could be an issue of life and death for him and his family.
And, it goes without saying that there are millions and millions of individuals who have money, power and influence that bad guys would not hesitate to spend their resources to pursue
Moreover, we know of the tragic events that actually happened – https://www.valuewalk.com/2018/02/biometrics-aadhaar-danger/
In this article we referred to an ill-thought deployment of biometrics with an explanation with graphs of what are false rejection and false acceptance.
As such, it is really sad to see so many people being (mis)led to believe that, although biometrics may be a threat to privacy, the biometrics must be supported by governments and citizens because biometrics contributes substantially to better security. This is a big myth that must be busted.
#identity #authentication #password #security #safety #biometrics #ethic #privacy #civilrights #democracy
Hitoshi Kokumaiの記事
ブログを見る
Some friends directed my attention to this news report - · “Biometric auth bypassed using fingerpri ...

Another topic for today is “Passwordless made simple with user empowerment” · https://www.securitym ...

Bad guys, who have a quantum computer at hand, would still have to break the part of user authentica ...
関連プロフェッショナル
この職種に興味がある方はこちら
-

介護職・ヘルパー(神奈川県横浜市旭区
次の場所にあります: Whatjobs JP C2 - 3日前
医療法人社団 司命堂会 介護老人保健施設 希望の森 横浜市 旭区, 日本【おすすめポイント】 · 介護老人保健施設での介護業務 職員食堂あり/働きやすさ 幅広い世代のスタッフが活躍しています · スタッフ同士が協力し合いながら業務に取り組む明るい職場なので、働きやすさも抜群です · 【仕事内容】 · 入所定員160名、全室個室のユニット型老健にて介護業務全般に従事していただきます。 経験の浅い方やブランクがある方も歓迎施設内外研修があり、着実にスキルアップが図れますよ 職員食堂があり昼食は300円、夜勤時は無料で食事が食べられます · 経験に自信がない方もOKお仕事に慣れるまで、しっかりとサポートいたします。 · 【必要資格 ...
-

未経験歓迎】外資系ホテルでのお客様対応★入社祝金最大20万円★
次の場所にあります: beBee S2 JP - 2日前
ALACOM CO.,LTD. Chuo, 日本◆◇高級ホテル施設警備◇◆ · 1出入管理 · 来館者に対しての受付対応を行います。 · 2巡回 · 施設内外を固定ルートで見回る業務です。 · 電球切れ、不審物などの確認を行います。 · 3防災センター業務 · 館内各所に設置された防犯カメラのモニターの監視業務や · 拾得物、遺失物の管理業務等があります。 · 4お客様の対応やご案内 · ・各業務を1時間程度の交代制で実施します。 · ・その他に、付帯業務が発生する場合があります。 ...
-

一般事務/旅行業
次の場所にあります: Whatjobs JP C2 - 4日前
株式会社リクルートスタッフィング Osaka, 日本NEW(本日掲載) · 派遣 · 【直接雇用の実績有】【超大手旅行会社】【服装自由】【時短相談可】【残業なし】【電話... · 一般事務 · 【時給】1,500円 ~ · 本町駅徒歩3分堺筋本町駅徒歩1分 · ここがポイント · 【直接雇用の実績有】【超大手旅行会社】【服装自由】【時短相談可】【残業なし】【電話少な目】 · - 綺麗なオフィス環境です · - 活気のある環境で働きたい方におすすめ · 長期 · 未経験歓迎 · 即日OK · 土日休 · 日数相談可 · 時間相談可 · 残業なし 大手企業 駅5分以内 · 服装自由 · Excel基礎 · 勤 ...
コメント
Debesh Choudhury
4年前 #1