Sequel - Detection of Fake Log-In Page

In my earlier post “Detection of FakeLog-In Page”, I wrote “show the user’s image ALONG WITH DOZENS OF OTHER IMAGES.”
Have you taken note of it? This element plays a crucial role in our scheme.
A would-be phisher can easily copy the log-in screen and show it to a target user whose User ID is known. But the phisher does not know which image was registered by the user as the credential of the genuine log-in server as against the other images, whereas both the user and the genuine log-in server know which one was registered.
We ask the user to pick up the registered image and also several other meaningless images in a random sequence; the outcome will be that the genuine log-in server will know that the user has selected the registered image in the choice, while a fake log-in server will not know it, so the phishing process will have to stop there. Copying the genuine log-in page would thus take the phisher nowhere.
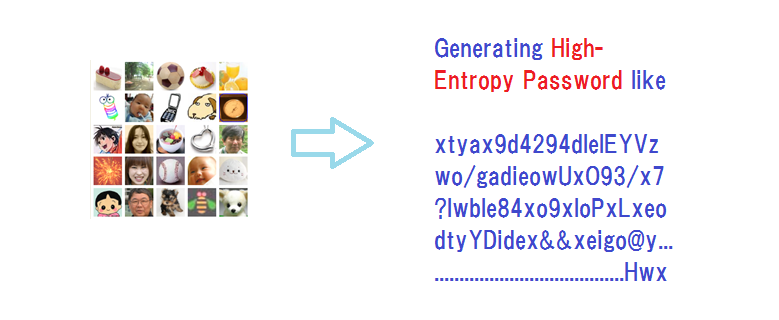
After this screening of fake log-in servers, the user will be asked to go through the authentication by a password, desirably by Expanded Password System where it is available.

< References >
Summary and Brief History - Expanded Password System
Image-to-Code Conversion by Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Negative Security Effect of Biometrics Deployed in Cyberspace
Removal of Passwords and Its Security Effect
Update: Questions and Answers - Expanded Password System and Related Issues (30/June/2020)
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
< Latest Media Articles Published in 2020 Spring>
Digital Identity – Anything Used Correctly Is Useful https://www.valuewalk.com/2020/05/digital-identity-biometrics-use/
‘Easy-to-Remember’ is one thing ‘Hard-to-Forget’ is another https://www.paymentsjournal.com/easy-to-remember-is-one-thing-hard-to-forget-is-another/
Hitoshi Kokumaiの記事
ブログを見る
I take up this report today - “Facebook's metaverse plans labelled as 'dystopian' and 'a bad idea'” ...
“Expanded Password System is no bad, but we do not need it. · We can rely on password managers that ...

Bad guys, who have a quantum computer at hand, would still have to break the part of user authentica ...
関連プロフェッショナル
この職種に興味がある方はこちら
-

フォークリフト・クレーン
次の場所にあります: beBee S2 JP - 4日前
株式会社テクノ・サービス 足利市, 日本 TEMPORARY株式会社テクノ・サービス/お仕事No/0780940 · 充填・包装・機械操作 · ====仕事内容==== · ミネラルウォーターの充填、包装、機械操作作業をお願いします。(派遣) · *ライン作業です · ====給料==== · 時給1200円交通費全額支給 · ====勤務地==== · ■勤務エリア · 栃木県足利市 ...
-

塾講師 アルバイト 個別指導
次の場所にあります: beBee S2 JP - 1週間前
個別指導学院ヒーローズ和泉室堂校 和泉市, 日本 パートタイム雇用形態 · アルバイト · 職種・指導形態 · 個別指導 · 1~5名を対象とした個別指導 · 給与 · 時給1,200円 · アルバイト講師の組織化を進めています。目指せ講師リーダー · 最寄駅 · 光明池駅より徒歩22分 · 和泉中央駅より徒歩28分 · 待遇 · アルバイト講師の中にも役職を設けており、役職に応じて昇給します。 · 交通費支給 昇給あり 研修制度充実 · 仕事内容 · 様々な学習レベルの生徒さん、様々な性格の生徒さん、様々な目標の生徒さん、そんな様々な目的にあわせた個別指導を行なっております。 · 「勉強が嫌い」と言う生徒さんか ...
-

保育士
次の場所にあります: Whatjobs JP C2 - 2日前
ドリームキッズ 花南保育園 Tokyo, 日本**タイトル**: · 保育士 · **このお仕事の特徴**: · 急募 即日勤務OK · **勤務先名**: · ドリームキッズ 花南保育園 · **職種**: · 保育士 · **仕事内容**: · 西武新宿線「花小金井駅」より徒歩7分 サポート体制万全ブランクある方も安心して働けます残業ほぼ無し週休2日なのでプライベートも充実 · **勤務地**: · 東京都小平市花小金井南町1-8-10 · **給与**: · 【月給】201,700円 ~【その他手当】 超勤手当 在籍児童数加算手当 交通費全額支給 昇給あり 賞与 年2回(3ヶ月分) ※経験者優 ...
コメント
Ricci Burgett
3年前 #1