Removal of Passwords and Its Security Effect
Assume that the password has been removed from digital identity. Then digital identity platforms would have only two authenticators - physical tokens and biometrics.
Biometrics by its nature requires a fallback measure against false rejection, and only the physical token could be the fallback measure for biometrics here. We have only two scenarios.
(1) authentication by a physical token, with an option of adding another token. Its security effect is plainly illustrated below.

(2) authentication by a biometrics deployed in ‘multi-entrance’ method with a physical token as the fallback measure, with an option of adding another token. Its security is even lower than (1) as quantitatively examined at https://www.bebee.com/producer/@hitoshi-kokumai/quantitative-examination-of-multiple-authenticator-deployment
We reckon that quite a few professionals of cyber security and identity management are well aware of these facts but something seems to prevent them from speaking out. Possibly, once they had touted those powerless solutions and recommendations to millions of clients, it might be embarrassing to admit the facts.
But it’s never too late to return. They are expected to speak out.
< Excerpt from Quantitative Examination .... >
Vulnerability (attack surface) of an authenticator is generally presented as a figure between 0 and 1. The larger the figure is, the larger the attack surface is, i.e., the more vulnerable. Assume, for instance, as just a thought experiment, that the vulnerability of the PKI-enabled token (x) be 1/10,000 and that of the password (y) be 10 times more vulnerable, say. 1/1,000. When the two are deployed in ‘multi-layer’ method, the total vulnerability (attack surface) is the product of the two, say, (x) and (y) multiplied. The figure of 1/10,000,000 means it is 1,000 times more secure than (x) alone.
On the other hand, when the two are authenticators deployed in ‘multi-entrance’ method, the total vulnerability (attack surface) is obtained by (x) + (y) – (xy), approximately 0.0011. It is about 11 times less secure than (x) alone.
So long as the figures are below 1, whatever figures are given to (x) and (y), deployment of 2 authenticators in ‘multi-layer’ method brings higher security while ‘multi-entrance’ deployment brings lower security. As such ‘multi-layer’ and ‘multi-entrance’ must be distinctly separated when talking about security effects of multiple authenticators.
The same calculation applies to biometrics used in cyber space where it has to rely on a fallback password/PIN deployed in ‘multi-entrance’ method against false rejection. You might assume that biometrics deployed with a password/PIN in ‘multi-layer’ method should bring us a very high security. But, very sadly, this scenario never comes true. When rejected by biometrics, what can we do? We will only see that we are unable to login even if we can feed our password/PIN.
< Related Articles >
Big Myths in Digital Identity
History, Current Status and Future Scenarios of Expanded Password System
Hitoshi Kokumaiの記事
ブログを見る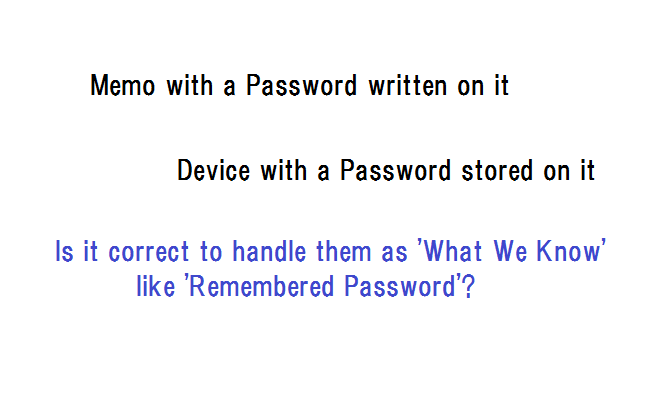
I got interested in this article -on the password problem · “Tech Q&A” · https://www.unionleader.c ...

I today take up this The Register report - “Client-side content scanning as an unworkable, insecure ...

Some friends directed my attention to this news report - · “Biometric auth bypassed using fingerpri ...
この職種に興味がある方はこちら
-

有料老人ホーム 看護職員
次の場所にあります: Whatjobs JP C2 - 6日前
ニチイケアセンター練馬さくら台(池袋支店) Tokyo, 日本**有料老人ホーム 看護職員** · バイク通勤OK子ども手当あり ニチイケアセンター練馬さくら台で一緒に働きませんか · **勤務先**: ニチイケアセンター練馬さくら台(池袋支店) · **給与**: 時給1860~1960円 · **勤務地**: 東京都 練馬区 · **アクセス**: 西武池袋線桜台駅 徒歩10分 · **時間**: 週1日以上 · **【オススメポイント】** · 看護スタッフを募集しています · ニチイケアセンター練馬さくら台は、スタッフ同士が仲が良く幅広い年齢層のスタッフが活躍しています。 · プライベートの話しを和気あいあ ...
-

一般事務/不動産業
次の場所にあります: Whatjobs JP C2 - 1週間前
株式会社リクルートスタッフィング Osaka, 日本NEW(本日掲載) · 派遣 · 【人気の扶養枠内OK 直接雇用の可能性あり】 · - 地域密着の不動産会社で事務のお仕... · 一般事務 · 【時給】1,350円 ~ · 喜連瓜破駅徒歩1分長居(地下鉄)駅徒歩2分バス14分 · ここがポイント · 【人気の扶養枠内OK 直接雇用の可能性あり】 · - 地域密着の不動産会社で事務のお仕事 · - 駅近徒歩1分、自転車通勤OK · - 少人数のアットホームな職場です/社員さんもいい人ばかり · - ネイル髪色自由 · 長期 · 未経験歓迎 · 即日OK · 土日休 平日休 · 日数相談可 · 時間相談可 ...
-

ネイリスト
次の場所にあります: beBee S2 JP - 2日前
【社名非公開求人】ホテルのフロントスタッフ 京都市下京区, 日本 契約社員 正社員更新日: · 【業務内容】ホテルのフロントスタッフ■チェックイン・アウトの対応や宿泊予約チェック■客室からの連絡への対応等 · 【雇用形態】 契約社員 正社員 · 【勤務地】京都府内のホテル · 【給与】月給 180,000円~260,000円 · ※エリアにより給与変動あり · ※時給制の契約社員もございます。詳細につきましてはご応募時にお伝えします。 · 【試用期間中給与】※規定に準ずる · 【PR】先輩スタッフが丁寧にあなたを指導♬ · 接客・接遇のマナーや正しい敬語、臨機応変な対応など、たくさんのスキルが身につきます · 【休日】月8日休み(シ ...
コメント