Rapid Increase in Military Use of Expanded Password System
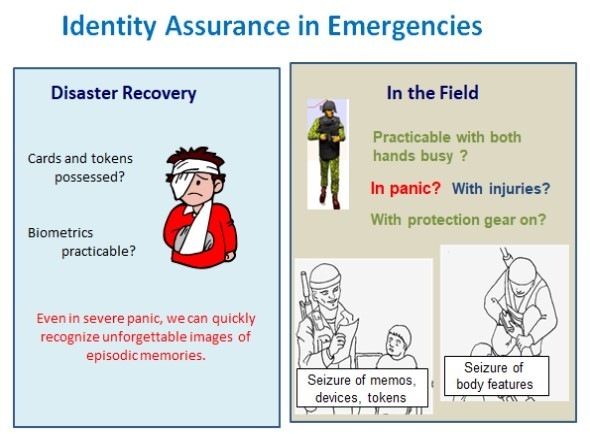
As for the versatile practicability of Expanded Password System, we now can refer to the trouble-free military use in the most demanding environment, with the users having increased 10-fold over the 7-year period from 2013 to 2020 and predicted to increase further; Images of toys, dolls, dogs and cats, for example, that our children used to love for years would jump into our eye even when we are placed in heavy pressure and caught in severe panic.
What is practicable in the most demanding environment for the most demanding application can be easily practiced in everyday environments for everyday applications; the reverse is not true, though.
Such an authentication system that copes with the panicky situations can be operated for all the everyday applications, too, as a stand-alone authenticator, as a factor of multi-factor schemes and as the master password of ID federation schemes.
The panic-proof feature of Expanded Password System is also discussed here – “Availability-First Approach”
With respect to this subject, I would like to refer to the proposition that we submitted to Armed Forces Communications and Electronics Association (AFCEA).
AFCEA called for propositions for ‘2020 Solution Review Problem Sets’ which was intended to answer to U.S. Army Chief Information Officer who is seeking solutions to emerging or existing challenges.
We submitted an abstract of our proposition for Item #3 and were notified that our abstract is kept on-file as a backup and will be included in the compendium of the abstracts that is made available to CIO/G6 leadership. We are very pleased to see this positive development.
As mentioned in the abstract, our proposition is not a hypothesis, but is substantiated by the trouble-free military use in the field from 2013 till now with the number of users increasing 10-fold and set to continue to increase further.

Hitoshi Kokumaiの記事
ブログを見る
We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password sys ...

The quantum computer held in a bad guy’s hand is indeed a big threat. So is the artificial intellige ...

I today take up this The Register report - “Client-side content scanning as an unworkable, insecure ...
関連プロフェッショナル
この職種に興味がある方はこちら
-

クリエイティブ系
次の場所にあります: Whatjobs JP C2 - 3日前
株式会社レゾナゲート Tokyo, 日本掲載日:2023/11/30 · 《在宅メイン》WEBメディアの編集や記事校正・執筆など · ここがポイント · @医療系WEBメディア企業/自由な社風 · メディア編集・メルマガ作成のサポートなど · - 業界最大手お医者様向けポータルサイト運営企業 今回は、メディア編集アシスタントのお仕事をおまかせしますライフスタイル関連の記事コンテンツの校正や執筆、進行管理などがメイン付随する出版社などの関連部門とのやり取りも多く発生するポジションですなんと業界経験は不問メディア編集のご経験を活かして医療業界でスキルアップしたい方も必見です社内は私服OKで、自由な ...
-

在宅配信業務
次の場所にあります: Whatjobs JP C2 - 3日前
㈱YUPO1 豊島区, 日本**採用詳細**: · **在宅配信業務**: · **ご応募をご検討いただいている皆様へ**: · 豊島区エリアで大募集 · ご応募いただいた際にメールをお送りしておりますのでご確認を宜しくお願い致します · 詳しくは下部応募後の流れをご確認ください · **募集項目**: · **勤務先**: · 東京本社 · **職種**: · 在宅配信業務 · **雇用形態**: · アルバイト · **仕事内容**: · 豊島にて在宅大募集 · 充実したサポート環境でお迎えいたします · 在宅配信業務をお任せ · 応募に面接..新しい仕事お探しって大変ですよね ...
-

会場設営撤去スタッフ
次の場所にあります: Whatjobs JP C2 - 3日前
株式会社ウエストサイド採用本部 江戸川区, 日本【職種名】 · 会場設営撤去スタッフ シフト自由 · **仕事内容**: · 登録制のアルバイトです · 初めての方でも簡単にできるお仕事を用意しています。 · **応募資格・条件**: · 必要な資格等はございません。 · **募集人数・募集背景**: · 8~12名募集 · **勤務地**: · 新宿支店 · 東京都江戸川区中葛西 · 最寄り駅:葛西駅 · **勤務時間**: · シフト制 · ご都合の良いスケジュールで勤務お願いしています。 · **給与**: · 時給 1150円 ~ 2000円 · **休日休暇**: · ご都合の良いスケジュー ...

コメント
Zacharias 🐝 Voulgaris
4年前 #3
Cool. If you are interested in a more robust algorithm, coupled with another that can guarantee randomness in the encryption keys used, I am happy to help. This is the last time I'm going to offer this as it seems that all my previous attempts (e.g. suggesting collaboration on Cybersecurity matters) didn't get the message through. Cheers!
Hitoshi Kokumai
4年前 #2
As for the military use case mentioned in my article, our software is protected by encryption as well as protecting encryption, but all that I know is that it is perhaps a proprietary algorithm that is not publicized.
Zacharias 🐝 Voulgaris
4年前 #1