Does US Army Really Want to Bring Down Security?

US Army looks to use soldiers’ biometric data to secure wearable tech
The US Army appears to be misguided.
We would not need to worry much if they intend to deploy biometrics for ‘IDENTIFICATION’ of soldiers.
We would have to worry a lot if they intend to deploy biometrics for ‘AUTHENTICATION’ of soldiers.
Contrary to the widespread misperception, biometrics used for authentication would only lower the digital identity security as demonstrated in this video - Biometrics in Cyber Space - "below-one" factor authentication https://youtu.be/wuhB5vxKYlg
and closed examined in this article – Negative Security Effect of Biometrics Deployed in Cyberspace
https://www.linkedin.com/pulse/negative-security-effect-biometrics-deployed-hitoshi-kokumai/
Should you have any contact with someone at US Army, you would be requested to convey this warning to them before it is too late.

It was in 2001 on the website of a globally reputed electronics manufacturer that I first noticed this awkward phenomenon. They alleged that their face biometrics was going to displace the password. It immediately occurred to me what we could do when the system failed to recognize us. I quickly started to search for an answer on their website and found a brief statement in a Q&A corner "Don't worry if you are not recognized. You can get logged in by feeding the password that you had registered earlier".
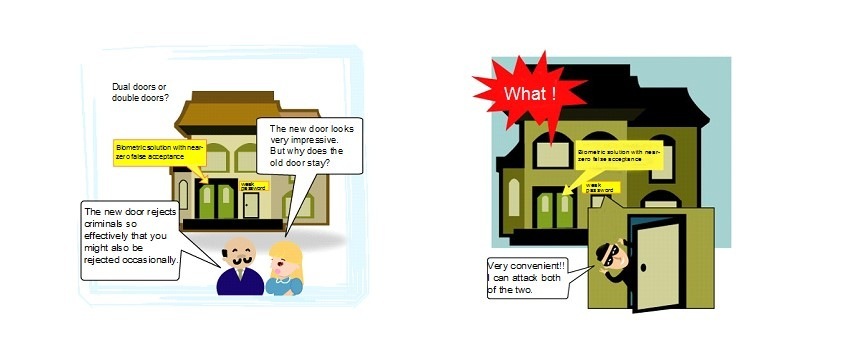
The second encounter came a few months later at a security conference where another global brand hung a large poster reading "Farewell to Password by Fingerprints". I asked an attendant "What can we do when rejected by the fingerprints sensor?", to which he replied "Don't worry. You can rescue yourself by feeding the password that had been registered earlier". I raised the next question "Then, how would it be possible for you to allege "Farewell to Password by Fingerprints?” The attendant turned silent and never opened his mouth again. I gave up and left there.
It has been as such since 2001 and still is.
Hitoshi Kokumaiの記事
ブログを見る
I take up this report today - “Facebook's metaverse plans labelled as 'dystopian' and 'a bad idea'” ...
We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password sys ...

Today's topic is this report - “How blockchain technology can create secure digital identities” · h ...
関連プロフェッショナル
この職種に興味がある方はこちら
-
短期2ヶ月 アパレル 販売スタッフ
次の場所にあります: Talent JP C2 - 4日前
Nプラス 川崎アゼリア店 Yokohama-shi, 日本仕事情報 · ● 仕事内容 ・アパレル販売スタッフ店内での接客・販売商品の荷受作業、商品の補充、店内清掃、事務作業、ディスプレイ商品の整理など※経験・知識は問いません。アパレル業界未経験の方も歓迎※ノルマもありません。 ●Nプラスって何? 私たち『Nプラス』は、ニトリグループ発のレディースファッションブランドです。年齢を重ねながらも若々しさや感性を失わない、大人の女性が毎日着たいと思うファッションを提案しています。まだ始まったばかりのこの事業を、私たちと一緒に作り上げていきませんか? ●アパレル未経験でも歓迎 「アパレル業界未経験の方」や、「仕事にブラ ...
-

スシロー 糸満西崎店
次の場所にあります: Talent JP C2 - 3日前
AKINDO SUSHIRO Itoman, 日本仕事情報 · ● 仕事内容 開店前は、イカやいくらなどのネタを解凍したり、揚げ物や · 茶わん蒸し等の仕込みなどをしてもらいます。オープン後は、 · にぎりや軍艦を作ったり、うどんやパフェなどのデザートを · 作ったり、レーンに流しお客様にお届けします。閉店後は、 · 食器や使用した器具の洗浄・厨房の清掃をします。 ●高校生、活躍中 「飲食店のバイトって、大変そう」と思っていませんか。 · スシローは、友達同士の応募も歓迎です。先輩スタッフが丁寧に · 教えるので安心して、ご応募してください。高校では出会う事の · できない、大学生や社会人の方も沢山働 ...
-
短期 家具・インテリア・雑貨専門店 売場スタッフ 短時間
次の場所にあります: Talent JP C2 - 4日前
ニトリ 名古屋金山山王店 Nagoya, 日本仕事情報 · ● 仕事内容 【ニトリ店内での接客スタッフ】短期間でより稼ぎたい人におススメのお仕事です。店舗での接客や品出し、季節に合わせたインテリア雑貨の陳列など。混雑状況に応じて、レジでの袋詰めなどのヘルプ業務も行っていただきます。 ●短時間での勤務 子供が学校から帰ってくるまでの時間帯で働きたい方。夕飯の仕度が間に合うように帰りたい方。家事の合間の隙間時間でちょっとだけ働きたい方。週20時間未満のお仕事ですので、扶養内での勤務が可能です。柔軟なシフト対応で働くママを応援します。 事業内容 · 家具・インテリア用品(ホームファニシング商品)の ...


コメント
mohammed khalaf
3年前 #3
Debesh Choudhury
3年前 #2
Debesh Choudhury
3年前 #1