Digital Identity and Democracy

When injured and panicked with empty hands in emergencies, how can we get authenticated securely and reliably?
It’s the obligation of democratic societies to provide citizens with the identity authentication measures that are practicable in disaster recovery and other emergencies.
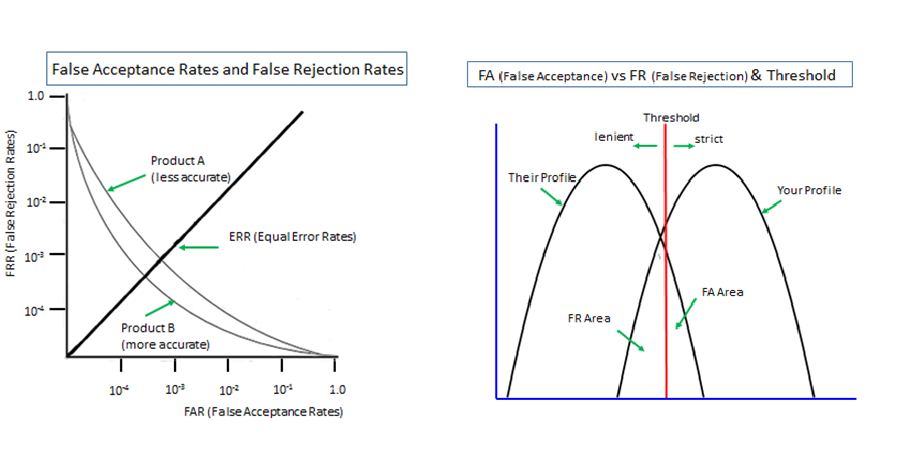
Authenticating empty-handed and injured people cannot be done without involving 'Shared Secrets'. Authenticating empty-handed, injured and panicked people cannot be achieved without involving 'Panic-proof Shared Secrets'. Physical tokens and biometrics do not help.
Enabling people to register their unforgettable non-text memories as their passwords could help a lot, possibly the only practical answer.
Expanded Password System enables it. What is practicable in panicky situations is easily practicable in everyday life, although the reverse is not always true.
It could also be noted that Expanded Password System can be flexibly implemented in multiple ways and methods. When packaged as an 'image-to-text converter ’module, it can be incorporated into the ubiquitous legacy text password systems for achieving better balance of security and convenience, easily, quickly and economically.
< Related Articles >
History, Current Status and Future Scenarios of Expanded Password System https://www.bebee.com/producer/@hitoshi-kokumai/history-current-status-and-future-scenarios-of-expanded-password-system
Slide – Identity Assurance in Emergencies https://www.slideshare.net/HitoshiKokumai/identity-assurance-in-emergencies
Big Myths in Digital Identity https://www.bebee.com/producer/@hitoshi-kokumai/big-myths-in-digital-identity
< Features of Expansion of Password System >
- It is not only stress-free for users but fun to use, as opposed to the dread and overhead that come today with creating, memorizing and storing passwords
- It turns a low-entropy password into high-entropy authentication data
- It eases the burden of managing the relationship between accounts and passwords
- It deters phishing attacks
- It can be deployed under any type of circumstance, including combat
- It supports existing schemes, such as:
- Biometrics which require passwords as a fallback means
- Two/multi-factor authentications that require passwords as one of the factors
- ID Federations such as password managers and single-sign-on services that require passwords as the master-password
- Simple pictorial/emoji-passwords and patterns-on-grid can be deployed on this platform.
- It is relevant whenever text passwords and pin numbers are in use
- And, nothing would be lost for people who want to keep using text passwords
- Last but not least, it continues to rely on free will.
Hitoshi Kokumaiの記事
ブログを見る
Today's topic is this report - “How blockchain technology can create secure digital identities” · h ...

Today's topic is BBC's “Facebook to end use of facial recognition software” · https://www.bbc.com/n ...
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...
この職種に興味がある方はこちら
-
仕分けスタッフ/4h~8h/週5日シフト制【アルバイト・パート】
次の場所にあります: Talent JP C2 - 1週間前
川越西郵便局 Kawagoe, 日本 週5日以上お仕事内容 · ●局内作業スタッフ● · 郵便物等を配達地域別に仕分けるお仕事です · ※事前研修やしっかりとしたサポートがあります♪ 初めての方も安心です · 給与時給1,010円~1,170円 · ※採用時の時給1,010円 · ※年2回のスキル評価結果により最高時給1,170円まで可能です · ※34567+夜間割増賃金有(1勤務につき200円支給) · ※45678+深夜割増賃金有(休憩時間を除く22:00~5:00の時間帯は基本時給の割増率50%) · 勤務地埼玉県川越市小室22-1 · 地図受付・勤務地はこちら · 勤務期間〇6か月以上の ...
-
栄養士】お子さんのお休みに合わせて働けます♪
次の場所にあります: Talent JP C2 - 6日前
株式会社レパスト Kitakyushu, 日本 アルバイト・パートお仕事情報 · お仕事内容 ≪お仕事内容≫ · ◇食材カット · ◇給食の配缶 · ◇食器洗浄 など · 「料理が好き」「栄養士・調理師の経験を活かしたい」...そんな方にもオススメ。 · 給与 時給1,000円~ · *経験考慮 · *当社規定有 · ◆支払い方法:月1回 · ◆交通費:一部支給 · *当社規定有 · 勤務地 福岡県 北九州市小倉北区 昭和町16番1号 · 地図を確認 · アクセス ◆モノレール小倉線 香春口三萩野駅 徒歩 5分 · 勤務期間 長期(3ヶ月以上) · *長期勤務できる方、大歓迎 · シフト・勤務時間 ...
-

派/コスメショップ/販売スタッフ
次の場所にあります: Whatjobs JP C2 - 3日前
ファッション人材リンク株式会社 第一事業部 Yokohama, 日本**《勤務地》**: · 神奈川県横浜市西区横浜ポルタ · **《メリット》**: · 未経験OK,服装自由,日払い・週払い,社員登用あり,高収入,髪型自由,主婦・主夫歓迎,フリーター歓迎,オススメ,即日勤務OK,シフト制,駅チカ・駅ナカ,交通費支給 · **《お仕事の特徴》**: · 20~30代の女性スタッフさん活躍中人気のコスメSHOPで美容部員さん大募集日・週払いOK · まずは履歴書不要の簡単登録から髪・ネイル自由/短期/短時間/オープニング店舗など選べるお仕事たくさんなんでも相談OK · **《仕事内容》**: · 接客、在庫管理、カウンセリ ...


コメント