Deterrence to Hard-to-Defend Phishing Attacks
It is known that targeted/spear phishing attacks often bring grave damages as the consequences. Implementation of Expanded Password System is expected to deter the indiscriminate mass phishing attacks to a large extent.
However, all the passwords, whether texts, patterns or images, are vulnerable to Spear/Targeted Phishing, whatever tricks we may incorporate into them and that effective deterrence could be expected only when we involve 2-channels or 2-steps or both.
Incidentally, that the password is vulnerable to spear/targeted phishing does not mean that removing the password makes a solution. It is the same as removing a lock/key and enhancing the door panel does not make a solution to the vulnerability of the lock/key.
A. Against Indiscriminate Mass Phishing
Where the users are encouraged to create their own unique image matrices with Expanded Password System (*1) is deployed, we could assume that criminals feel discouraged about the indiscriminate mass phishing.
*1
It would be a costly job, if technically possible, to capture thousands, millions or billions of image matrices unique to all the different userIDs from the genuine authentication servers, copy them on the criminals' fake servers, get them activated for detecting tapping and clicking on the screen and then try to lure the target people into disclosing their credential (the registered images) on the criminals' fake servers by sending phishing mails, etc.
Effective against indiscriminate mass phishing, though not effective against the spear/targeted phishing.
B. Against Spear/Targeted Phishing
2-Channel Expanded Password System (implemented as Onetime MnemonicGuard *2) could discourage criminals because the criminals would need to place both of the two channels under their control simultaneously before starting the phishing trial.
*2 https://www.slideshare.net/HitoshiKokumai/2factor-authentication-with-no-physical-tokens-and-no-sms
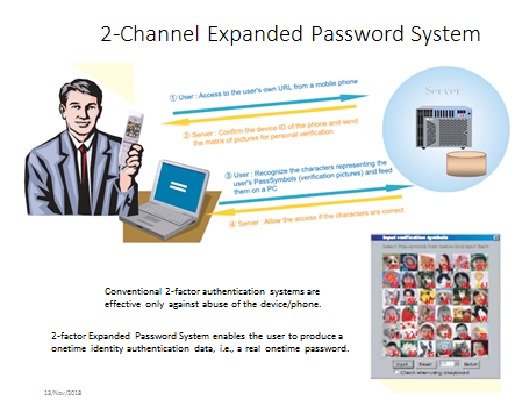
Alternatively, where 2-factor/channel system is not implemented but Expanded Password System (EPS hereafter) is deployed, we could think of adding a second step of EPS making the system 'Selective 2-step EPS' for the users who opt for it.
With the 2-step EPS, the image matrix for the 2nd step is supposed to be shown to the user/criminal only when the user/criminal has gone through the 1st step EPS.
The optional 2-step EPS could discourage criminals by way of making it hard for the criminals, who have somehow obtained the credentials (the registered images) of the target persons for the 1st step EPS, to prepare the image matrices of the 2nd step EPS on the criminals' fake servers quickly enough.
Specifically speaking, a criminal who knows the userID of the target person can capture the image matrix of the 1st step EPS from the genuine server without the target's knowledge, prepare the image matrix of the target and lure the target into disclosing the credential (the registered images).
However, the criminal would then have a huge difficulty in obtaining the credential (the registered images) for the 2nd step ESP unless the criminal has a magical power of completing the following process in a matter of seconds -
Having successfully stolen the credential for the 1st step,
1. access the target's account with the target's UserID and get the target's image matrix shown,
2. visually locate and manually tap/click the images of the target's selection on the screen of the genuine server,
3. successfully going through it, capture the target's image matrix for the 2nd step EPS,
4. activate the image matrix on the criminal's fake server so that it can detect tapping/clicking by the target,
5. show the image matrix and urge the target to select the credential (the registered images) forthe 2nd step EPS.
Users, who had been informed that they should suspect the act of phishing if they are kept waiting for more than a few seconds after the clearance of the 1st step, would be advised to cut off the connection without moving to the 2nd step and re-create the different image matrix for the 2nd step EPS.
As such, the burden forced upon criminals is very heavy, whereas the burdens on the authentication server and the users are relatively lighter.
The authentication server is required to add another step of EPS to the default EPS for the users who opt for an additional protection against spear/targeted phishing.
The users who opt for the 2-step EPS are required to create two sets of image matrices and remember the advice that they should cut off the connection without moving to the 2nd step when they are kept waiting for more than a few seconds after clearing the 1st step and re-create a new image matrix for the 2nd step, desirably the one for the 1st step as well.
Whether or not this is too heavy a burden for the users may well be dependent on the value of the information asset that they have access to. Managers of classified and highly sensitive information in large volume probably do not view it as too much a burden in view of the grave damages as the consequences of spear/targeted phishing attacks.
C. Against Persistent Spear/Targeted Phishing
Criminals who persistently chase really valuable information assets could be discouraged if we deploy the 2-step EPS coupled with the 2-Channel method.
Remark: The core concept of the above proposition was first announced 12 years ago when I was a member of Japan’s Anti-Phishing Task Force organized by the government.
The anti-phishing task force, which was dominated by vendors of biometrics, PKI and anti-virus software, did not show any interest in this proposition. Dissatisfied, I quit it and have since forgotten about it.
I was reminded of this long-forgotten proposition by a brief reference to ‘Phishing’ in a comment from gentleman with respect to my latest article
https://www.linkedin.com/pulse/takeaways-from-consumer-identity-world-europe-2018-hitoshi-kokumai
Hitoshi Kokumaiの記事
ブログを見る
“Expanded Password System is no bad, but we do not need it. · We can rely on password managers that ...

Some friends directed my attention to this news report - · “Biometric auth bypassed using fingerpri ...

Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...
この職種に興味がある方はこちら
-
セブン-イレブン 横浜杉田3丁目店
次の場所にあります: Talent JP C2 - 2日前
株式会社セブン - イレブン・ジャパン Yokohama, 日本商品の陳列、ドリンクの補充、ホットスナックの調理など、徐々に仕事を覚えたら、商品の発注なども、お任せします。 · セブン-イレブンのコンビニスタッフ求人です。レジでの接客販売、商品の補充や陳列・簡単な清掃からはじまり、慣れてきたら、商品発注やキャンペーンのリーダーなども徐々にお任せします。売れ筋商品のチェックや、POPの作成も大事な仕事です。仕事は丁寧にお教えしますので安心してご応募ください。 · ...
-

ナイトマネージャー
次の場所にあります: Talent JP C2 - 2日前
公開範囲1.等を含む求人情報を公開する Rokkasho, 日本 パート仕事内容 · マエダストア六ヶ所店におけるナイトマネージャー業務全般を担当 · していただきます。 · ・値引き処理業務 · ・商品補充、前出し・商品の後始末 · ・防犯関連業務(店内外の見回り、店舗の施錠等) · ・レジ周りの応援、クレーム対応 · ・その他付随する業務 · ※土曜日、日曜日、祝日勤務できる方を希望します。 雇用形態 パート労働者 正社員登用の有無 あり 正社員登用の実績(過去3年間) 5名登用 派遣・請負等 就業形態 派遣・請負ではない 雇用期間 雇用期間の定めあり(4ヶ月未満) 2ヶ月 ...
-

調剤薬局での受付や調剤事務
次の場所にあります: Whatjobs JP C2 - 5日前
株式会社サエラファーマシーズ 同仁薬局 Osaka, 日本【募集概要】 · JR高槻駅より徒歩7分 · 同仁薬局で調剤事務を募集しています。 · 求人のPOINT · (1)月給 19~25万 · (2)賞与 計3ヶ月分 · (3)残業月5~10時間 · (4)年間休日117日 · (5)産休・育休取得実績多数あり · 医療機関でのお仕事は景気に左右されにくく · ライフスタイルが変わっても · 長く続けることができるのも大きな魅力です。 · ~新型コロナウイルス感染症対策について~ · 来社不要。パソコン・スマホでOK · お仕事の紹介はWEBまたは電話面談を実施しております。 · ご自宅からURLクリックの ...

コメント