Children’s Passwords Managed by Schools

A friend of mine brought me to this article. I took this phenomenon as a warning on the difficulty of having children manage their passwords.
Adults often fail to manage their text passwords. It is not hard to imagine what would happen if we force children to manage their text passwords by themselves, especially where they are told to use strong passwords; teachers would be wasting a vast amount of time for the frequent password reset, with much less time left for educating children.
Removing the password and bringing in biometrics would only make the matter worse as discussed here – “Removal of Passwords and Its Security Effect”
The lesson we should extract from this episode is that children should be offered a non-text password system that they can easily use without teachers' intervention. Our proposition is “Summary and Brief History - Expanded Password System” https://www.linkedin.com/pulse/summary-brief-history-expanded-password-system-hitoshi-kokumai
Body features are no more than body features
Can you be happy to see your external body features declared to be ‘what you are’?
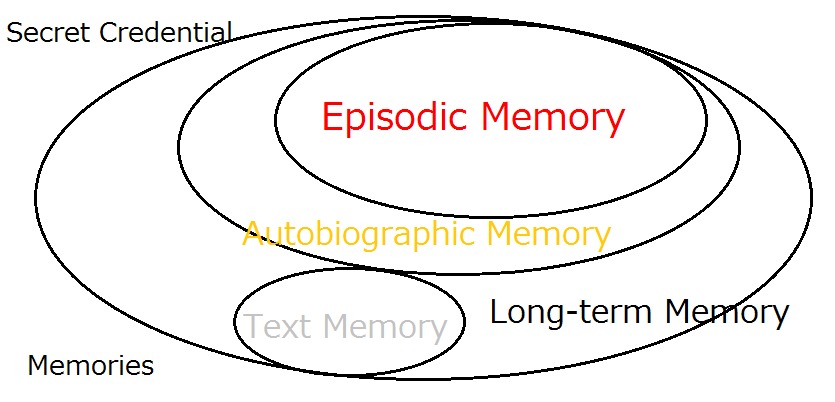
Quite a few security experts have long asserted that there are three components for identity authentication – ‘What We Remember’ (Secret Credential), ‘What We Have’ (Tokens and Cards) and ‘What We Are (Body Features).
Feeding a correct secret credential is under our control. So is presenting a correct token or card to some extent. But our body features are just beyond our control. Wouldn’t it be more appropriate to call it ‘What Our Body Features Are’?
Furthermore, whether the secret credential is correct or not is ‘Yes or No’, in other words, it is deterministic. So are the token and card. But measurements of our body features give us the answer as X% probable and Y% improbable. It has to be inevitably probabilistic due to the inherent nature of body features of living animals that we can by no means put under our control.
‘What we remember’ and ‘What we have’, which are both deterministic, can be used together in a security-enhancing ‘two-layer’ deployment, whereas probabilistic ‘what our body features are’ can actually be used with another factor only in a security-lowering ‘two-entrance’ deployment.
As such we have now come to observe that we actually have two factors of ‘what we remember’ and ‘what we have’ as valid authenticators for identity assurance, with ‘what our body features are’ to be counted in cyberspace as an optional tool to increase convenience at the sacrifice of security.
It might sound a bit outrageous to the old school who have long taken it for granted that ‘what we are’ is made of our external body features. But we are confident that the public will agree with us at the end of the day.
What makes ‘What We Are’?
Cognitive science supports the observation that our sense of self is made of our memory, especially a part of our autobiographic memory named episodic memory. This observation of our identity is also supported by a number of philosophers. We can rely on these observations for stating that what makes ‘what we are’ is ‘what we remember’.
We may be a minority in the domain of cyber security and identity management at present, but it does not affect what is correct and what is wrong.
Hitoshi Kokumaiの記事
ブログを見る
I would like to take up this somewhat puzzling report - “Google advises passwords are good, spear ph ...

I today take up this The Register report - “Client-side content scanning as an unworkable, insecure ...
“Expanded Password System is no bad, but we do not need it. · We can rely on password managers that ...
この職種に興味がある方はこちら
-

朝食調理スタッフ
次の場所にあります: Whatjobs JP C2 - 1日前
有料老人ホーム パステル湯里 大阪市 湯里, 日本**午前中の3時間勤務週1日~勤務OK 朝食調理スタッフ募集** · **盛付、片付け程度です** · **採用情報** · **【掲載社名】** · 有料老人ホーム パステル湯里 · **【雇用形態】** · パート · **【職種】** · 朝食調理スタッフ · **【仕事内容】** · 簡単な温め・盛付など · - 食数は少なめ朝食35食程度です · 安心の嘉誠会グループ · 調理未経験者も大歓迎 · 〇未経験者OK · 〇ブランクOK · 〇ミドル・シニア世代活躍中 · 〇主婦(夫)活躍中 · 〇週1日からOK · 〇扶養内勤務OK · 〇お仕事 ...
-

調理・栄養関連
次の場所にあります: Whatjobs JP C2 - 3日前
光が丘四季の香小学校 Tokyo, 日本光が丘四季の香小学校 · 練馬区 / 光が丘駅(徒歩8分) · 【職種】 · 学校 · (正)調理師/栄養士・管理栄養士・フードコーディネーター · 【雇用形態】 · 正社員 · 【仕事内容】 · ※この求人情報は株式会社キャリアナビによる職業紹介になります。 · 小学校での給食調理のお仕事です。 · 調理・仕込み・配缶・洗浄・清掃・書類作成などの厨房業務全般をお願いします。 · 学校給食の経験がない方も一からしっかりとお教えいたしますので、 · 安心して働いていただけますよ。 · 学校でのお仕事のため、うれしい土日祝休み · さらに春・夏・冬休みもあり ...
-

調理師
次の場所にあります: Whatjobs JP C2 - 6日前
ケアホーム板橋 板橋区, 日本【職種名】 · 【調理師】小竹向原駅から徒歩5分のキレイな施設の直営厨房での勤務安心の大手医療グループです · **仕事内容**: · ケアホーム板橋は、2019年にオープンした複合型高齢者施設です。 · この度、直営厨房での調理師の募集をします。 · 厨房において、食材の仕込みや調理、盛り付けなどの調理全般をお願します。 · 施設を利用している利用者様に提供する食事と、施設で働いているスタッフに提供する食事を作っていただきます。 · 和・洋・中・郷土料理・各国料理・デザートなど、さまざまな種類の料理を提供しているため、幅広いジャンルの知識やスキルを身に ...
コメント