Account Recovery with Expanded Password System

Account recovery is a very tricky issue. It would be even trickier when it comes to the account recovery for decentralized/distributed digital identity systems with which we cannot rely on a central authentication server that can hold any volume of personal verification data.
What we need to take into consideration are
- The private key of a public/private key pair to be possessed by the user is supposed to play a critical role for the safe account recovery in decentralized/distributed digital identity.
- A cryptographic key stored on a device would be lost when the device is lost.
- Whatever physically exists can be physically stolen and abused.
- A valid account recovery solution must contain a valid authenticator in its process as the minimal requirement whether centralised or decentralised/distributed.
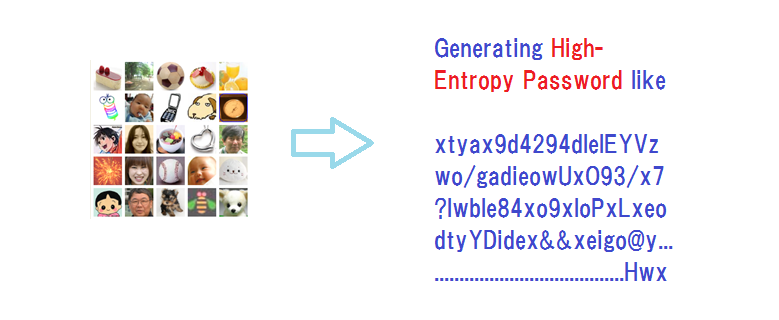
It is these observations that drove us to propose the re-generation of the private key on-the-fly from our image memory
There is nothing complex in the process of converting our image memory to a cryptographic key; Each image contains a large volume of unique data that works as the high-entropy image identifier. Alternatively, we can allocate a large volume of unique data to each image as the image identifier. Incidentally, alphabets and numbers are handled as the images.
When a set of multiple images are selected, whether in permutation or in combination, as the secret credential, the sum of the image identifier data will naturally have a unique and confidential data of a very high entropy that can work as the seed of a cryptographic key, whether symmetric or asymmetric.
The regenerated private key could be used as the element or one of the elements to get the account recovered. For practicality, users would be encouraged to have multiple copies of the image-to-code converter module and store them at multiple places.
A bad guy who has luckily grasped the software module would still face huge difficulties in finding the correct set of images to regenerate the correct private key and getting the legitimate user's account recovered for the bad guy to take it over. There are various techniques to hamper brute force attacks in both online and offline.
Where a private key is given by another party, a module containing a formula that turns the seed into the given private key should be added at the end of the image-to-code conversion. When designed as such, the program would eliminate the key along with all the halfway data when the program is shut down. The key no longer exists physically but can be regenerated from our memory at any time. This is the on-the-fly key regeneration by Expanded Password System.
This is not just a hypothesis. The ‘Image-to-Code Converter’ software to generate a cryptographic key had been completed and announced as ‘CyptoMnemo’ and ‘Authority-Distributed CryptoMnemo’ in 2004-2005 although we soon became unable to put it on the market due to the lack of budget. We could certainly consider the revival of the project with the latest safe coding technologies when we have secured the budget for it.
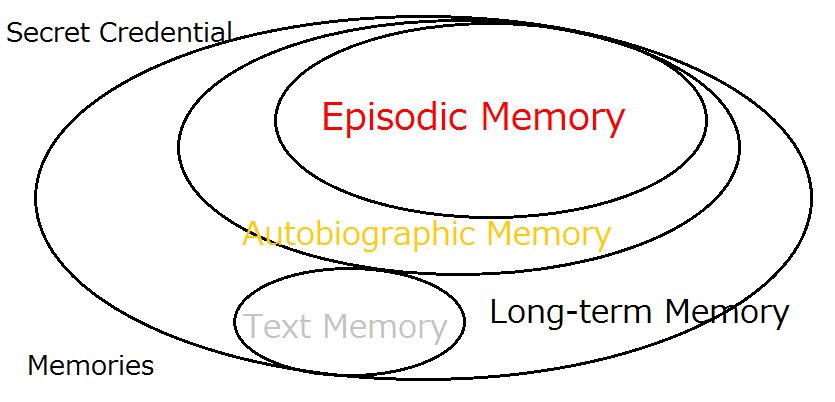
Last but not least, the essential point is that we do not rely on 'hard-to-remember' and 'easy-to-evaporate' text passwords but rely on 'hard-to-forget' and 'panic-proof' episodic image memory that had solidly fixed deep in our brain for many years as the original seed of the cryptographic keys.
< References >
Summary and Brief History - Expanded Password System
Image-to-Code Conversion by Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Negative Security Effect of Biometrics Deployed in Cyberspace
Hitoshi Kokumaiの記事
ブログを見る
https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...
“Expanded Password System is no bad, but we do not need it. · We can rely on password managers that ...
Our password headache may well be the consequence of these dual causes - · ‘Use of Impracticable Pas ...
この職種に興味がある方はこちら
-

商品のカウント
次の場所にあります: Whatjobs JP C2 - 4日前
ENtry,Ltd. 大阪市 北区, 日本**採用詳細**: · **商品のカウント**: · **おすすめポイント**: · \即日振込勤務した当日に給与GET/ · 365日/24h好きな時に給与がもらえる · 勤務後は、帰り道のATMで給与を受け取り · **募集項目**: · **勤務先**: · (株)エントリー 大阪支店 · **職種**: · 商品のカウント · **雇用形態**: · 派遣社員 · **仕事内容**: · - 1日だけ働きたい方も大歓迎学校帰りやお仕事帰りにもお勧め · - 未経験さん幅広い世代の方が活躍中- お仕事内容 · 商品のカウントをメインにお任せします。 ...
-
集配ドライバー4t 法人向け近距離の集荷と配達
次の場所にあります: Talent JP C2 - 4日前
福山通運株式会社 Kumamoto, 日本仕事情報 · ● 仕事内容 4tトラックの運転をしながら、担当エリア内の企業や商店を中心に集荷や配達等を行うお仕事。不安な方は、まずは2tトラックからスタートでも大歓迎です。同じエリア内で働くスタッフと班を作り、チームで協力し合いながら業務にあたります。大半は法人のお客様でルートはほぼ固定、長距離の運転もありません。 ●コミュニケーションが大切 集配ドライバーの仕事は、ただ荷物をお客様に届けるだけではありません。気持ちよくお届けして、喜んで受け取って頂くために、お客様に笑顔で接しながら配送を行うことがポイント。また、一緒に仕事を進める班員とのコミュニケ ...
-

電子部品組立作業員
次の場所にあります: Talent JP C2 - 1時間前
公開範囲1.等を含む求人情報を公開する Tohoku, 日本 パート仕事内容 · ◇電子部品の組み立て作業に従事していただきます。 · ・組立作業(電線に端子を圧着し、コネクタに挿入する) · ・ハンダ付作業 · ・目視による検査作業 · ・その他付随する業務 · *4~5名体制で稼働予定です。 雇用形態 パート労働者 正社員登用の有無 なし 派遣・請負等 就業形態 派遣・請負ではない 雇用期間 雇用期間の定めなし 就業場所 〒 青森県上北郡東北町大字上野字新堤向75-6 · ワークプロセス 上北工場 最寄り駅 青い森鉄道 上北町駅 最寄り駅から就業場所までの ...

コメント