#ethics
検索条件に合うグループがありません

Quantum Computing and Identity Assurance
Hitoshi Kokumai · Bad guys, who have a quantum computer at hand, would still have to break the part of user authentication that is not dependent on the public-key scheme, prior to accessing the target data, in the normal environment where secret credentials play a big role; quite a few cryptograph ...
New Slide - Healthy Second Life of Legacy Password Systems
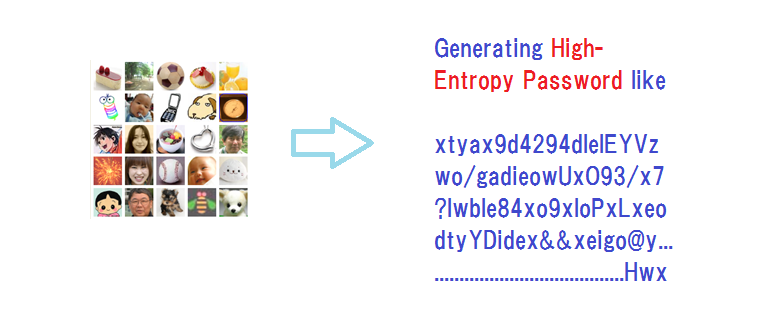
Hitoshi Kokumai · We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password system” · “We do not have to replace or rebuild the existing text password systems for making use of episodic memory; images of our episodic memory can be turned into a high-entropy c ...
関連プロフェッショナル
この職種に興味がある方はこちら
-

セラピスト / リフレクソロジー
次の場所にあります: beBee S2 JP - 4日前
【社名非公開求人】ホテルのフロントスタッフ さいたま市大宮区, 日本 契約社員 正社員更新日: · 【業務内容】ホテルのフロントスタッフ■チェックイン・アウトの対応や宿泊予約チェック■客室からの連絡への対応等 · 【雇用形態】 契約社員 正社員 · 【勤務地】埼玉県内のホテル · 【給与】月給 180,000円~260,000円 · ※エリアにより給与変動あり · ※時給制の契約社員もございます。詳細につきましてはご応募時にお伝えします。 · 【試用期間中給与】※規定に準ずる · 【PR】先輩スタッフが丁寧にあなたを指導♬ · 接客・接遇のマナーや正しい敬語、臨機応変な対応など、たくさんのスキルが身につきます · 【休日】月8日休み(シ ...
-

採用アシスタント
次の場所にあります: Whatjobs JP C2 - 2日前
株式会社アージスジャパン Tokyo, 日本\在宅勤務あり/人気のアパレルブランドでの採用アシスタント · 時給2400円+交通費英語力なし在宅も週3~4日など相談可能 · 冬のアウターといえばここダウンジャケットで有名なブランドでファッション誌でも多く取り上げられています今回は人事部門で店舗やオフィススタッフの採用アシスタントのお仕事です採用経験が活かせコミュニケーションスキルが活かせるお仕事です外資系ですが英語力いりまません感染症対策として出社と在宅勤務のハイブリッドになります在宅時に不明な点があればマネージャーとTeamsやメールでのやりとりなどコミュニケーションをとっています出社の場合も駅 ...
-

塾講師 アルバイト 個別指導
次の場所にあります: beBee S2 JP - 6日前
ITTO個別指導学院 深江南校 大阪市東成区, 日本 パートタイム雇用形態 · アルバイト · 職種・指導形態 · 個別指導 · 給与 · 1コマ80分1,712円 · ※上記コマ給はモデル給です · ※小学生の場合 · ※上記には最大10分までの授業準備時間を含む · ※指導人数により上記に人数手当(最大+100円)を加算 · ※授業時間については、50分・80分・100分があります · 最寄駅 · 新深江駅より徒歩11分 · 布施駅より徒歩15分 · 深江橋駅より徒歩9分 · 新深江交差点を内環状線沿いに北に500m。ローソン内環深江南1丁目店斜め向かい。 · 待遇 · 研修制度充実 · 仕事内容 · ●小学生、 ...
-
#seamlessdatabasemanagement 0 ポスト|ポスト
-
#power 0 ポスト|ポスト
-
#sqlserver 0 ポスト|ポスト
-
#sql 0 ポスト|ポスト
-
#sqlserverremotedbaservices 0 ポスト|ポスト
コンテンツを最大限に活用する

